Comprehensive Guide to Troubleshooting AWS Security Lake
A detailed walkthrough for troubleshooting common issues encountered with AWS Security Lake.
Shrishthi Dixit

Introduction to AWS Security Lake
AWS Security Lake is a vital service that consolidates and optimizes security data from across an organization’s AWS environments. Ensuring its proper functioning is crucial for maintaining robust security postures. This guide provides a detailed walkthrough for troubleshooting common issues encountered with AWS Security Lake.
Common Issues and Their Solutions
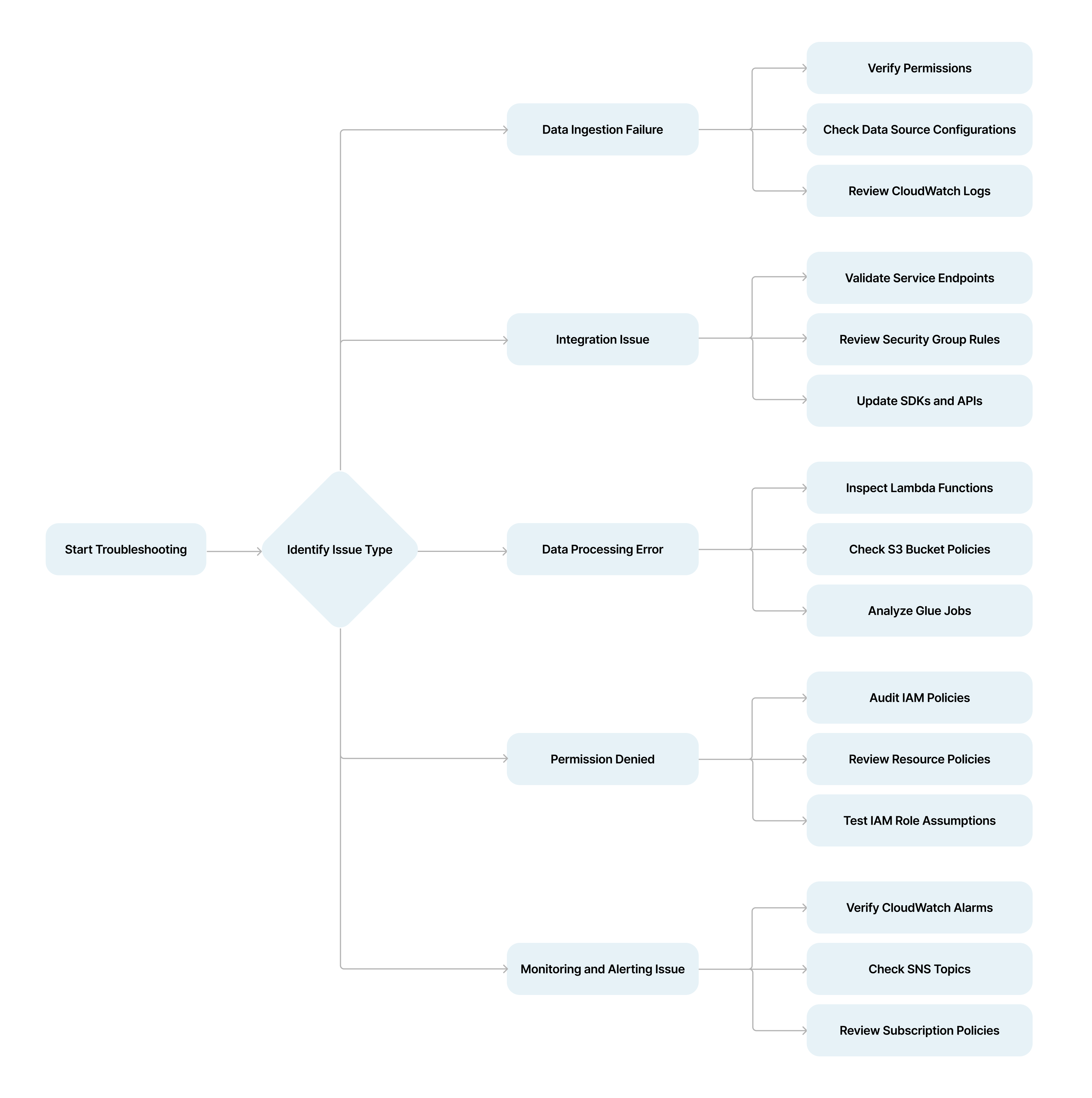
Data Ingestion Failures
Symptoms
Data ingestion failures can manifest as missing data, incomplete data sets, or error messages in the Security Lake console.
Troubleshooting Steps
1 - Verify Permissions: Ensure that the AWS Identity and Access Management (IAM) roles associated with your Security Lake have the necessary permissions to access and ingest data from your sources.

2 - Check Data Source Configuration: Confirm that the data sources are properly configured and connected to Security Lake.
3 - Review CloudWatch Logs: Analyze CloudWatch logs for any error messages or warnings related to data ingestion processes.
Integration Issues
Symptoms
Integration issues may prevent Security Lake from interacting seamlessly with other AWS services or third-party tools.
Troubleshooting Steps
- Validate Service Endpoints: Ensure that all required service endpoints are correctly configured and reachable.
- Review Security Group Rules: Check the security group rules to make sure they allow traffic between Security Lake and integrated services.
- Update SDKs and APIs: Ensure that you are using the latest versions of AWS SDKs and APIs that support Security Lake.
Data Processing Errors
Symptoms
Data processing errors can result in incomplete or incorrect data being stored in Security Lake.
Troubleshooting Steps
- Inspect Lambda Functions: Verify that any AWS Lambda functions used for data processing are executing correctly and without errors.
- Check S3 Bucket Policies: Ensure that the S3 bucket policies allow Security Lake to read from and write to the designated buckets.Note: only applicable when using user-created S3 buckets for Security Lake. Otherwise, Security Lake creates its buckets.
- Analyze Glue Jobs: If using AWS Glue for ETL processes, review the Glue job logs for any processing errors.
Permission Denied Errors
Symptoms
Permission-denied errors typically occur when Security Lake does not have the required access rights to resources.
Troubleshooting Steps
- Audit IAM Policies: Ensure that the IAM policies grant the necessary permissions for all required actions.
- Review Resource Policies: Check the policies of resources such as S3 buckets, Kinesis streams, and CloudWatch logs for correct permissions.
- Test IAM Role Assumptions: Validate that the IAM roles can assume the necessary roles and access the required resources.
Monitoring and Alerting Issues
Symptoms
Problems with monitoring and alerting can lead to missed notifications about Security Lake operations.
Troubleshooting Steps
- Verify CloudWatch Alarms: Ensure that CloudWatch alarms are set up correctly and monitoring the appropriate metrics.
- Check SNS Topics: Confirm that the Simple Notification Service (SNS) topics are configured to receive and forward alerts properly.
- Review Subscription Policies: Ensure that the subscription policies for SNS topics allow the necessary access and notifications.
Diagram for AWS Security Lake Troubleshooting Workflow
Conclusion
Effective troubleshooting of AWS Security Lake involves a systematic approach to identifying and resolving issues related to data ingestion, integration, data processing, permissions, and monitoring. By following the detailed steps outlined in this guide, organizations can maintain the reliability and security of their AWS environments.
About Metron:
Metron Security is a leading provider of custom-built and on-demand third-party integrations for security ecosystems and a trusted development partner for many top security companies, ranging from the fastest-growing to the largest enterprises. The team has worked on over 200 security applications and continues to develop new applications each month.
Metron is also the creator of the Security Exchange & Automation (SEA) platform, which allows end users to set up data exchange pipelines between security platforms rapidly.
For more information, visit www.metronlabs.com or reach out directly at connect@metronlabs.com.









