Enhance IoT/OT Security Visibility: Integrate Your Security Platform with Google SecOps
Learn how to integrate CI alerts into Google SecOps SIEM to boost IoT/OT visibility.
Anmol Jain

Security platforms with IoT-focused features like Cyber Watch (CW) and Cyber Insight (CI) are essential for identifying risks in connected devices within Operational Technology (OT) environments.
Google Security Operations (SecOps) provides SIEM capabilities for centralized threat analysis across your entire digital landscape. Integrating these two systems allows security teams to manage and analyze critical IoT/OT alerts effectively within their primary security operations console.
In this post, we’ll walk you through the process of integrating your security platform's CI alerts with Google SecOps SIEM, highlighting the key steps and benefits of using a third-party mediator like Bind Plane Agent.
Integration Overview: How it Works
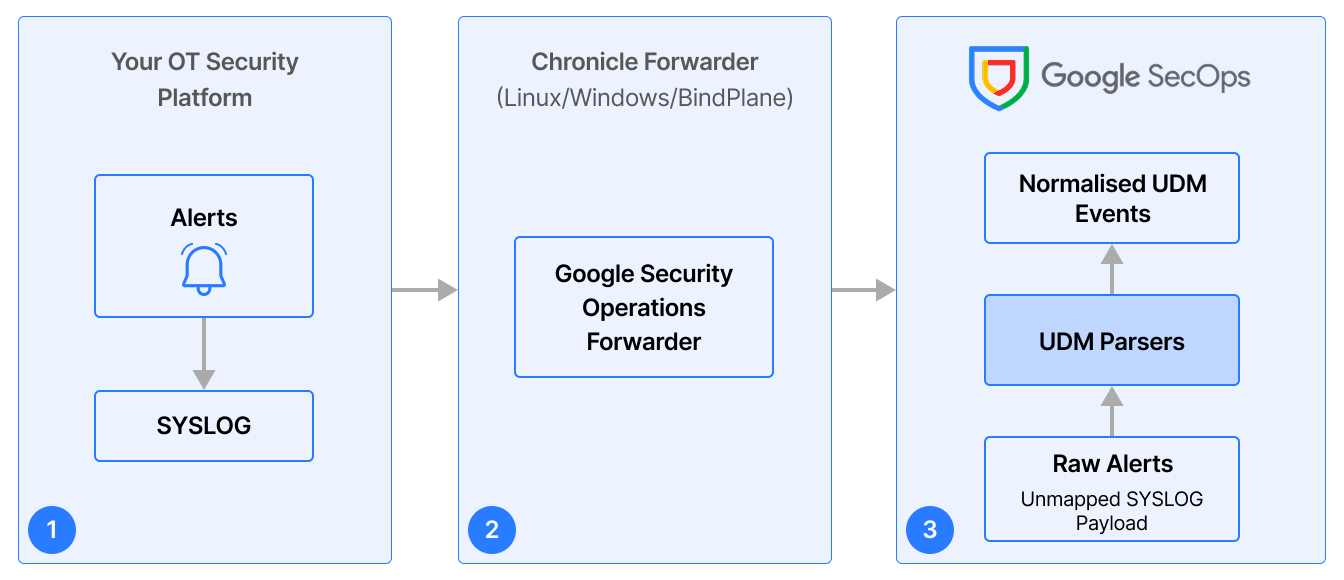
The integration relies on sending alerts from the security platform's CI modules to Google SecOps. A key component in this process is a data mediator, specifically a Bind Plane Agent, which handles the collection and forwarding of syslog data.
- Alert Generation: The OT Security platform (CI) detects security events and generates alerts.
- Syslog Forwarding: The security platform is configured to send these alerts as syslog messages.
- Data Reception (Bind Plane Agent - Receivers): The syslog messages are sent to the Bind Plane Agent, which is configured with a Receiver. This Receiver acts as a listening address (IP address and port) for incoming syslog data from the security platform.
- Data Processing (Bind Plane Agent - Service): The Bind Plane Agent's Service defines the data pipeline. It specifies that data received by the configured Receiver should be processed and sent to a specified Exporter.
- Data Export (Bind Plane Agent - Exporters): The Exporter within the Bind Plane Agent is configured with the necessary credentials for your Google SecOps instance. It is also configured with a specific log_type that identifies the source of the data (e.g., ot_security_platform_cyberinsight). This log-type in the Exporter should be the same as the metadata.log_type in Google SecOps.The Agent securely transmits the collected raw syslog data to Google SecOps using these details.
- Parsing & Normalization (Google SecOps - UDM Parser): Upon receiving the data, Google SecOps uses a custom parser, often developed specifically for the OT Security platform's alert format, to process the raw logs. This converts the raw data into the structured UDM format.
- Analysis: Normalized IoT/OT alerts appear as UDM events in Google SecOps, ready for analysis, correlation with other data sources, and investigation.
Integrating Your Security Platform with Google SecOps
Integrating these platforms significantly enhances your security visibility into the OT environment. Below is a step-by-step guide.
Prerequisites
- Security Platform Access: Administrative access to configure Syslog forwarding on your security platform.
- Google SecOps Instance: An active Google SecOps SIEM tenant.
- Bind Plane Agent Host: A Linux system (VM or physical) meeting Bind Plane Agent requirements (Docker, sufficient RAM/CPU/Disk).
- Network Configuration: Ensure network connectivity allowing the security platform to reach the Bind Plane Agent host via Syslog, and the Bind Plane Agent host to reach the Google SecOps cloud platform.
Integration Steps
- Configure Syslog Forwarding (on Security Platform):
- Navigate to the Syslog or alert forwarding settings within your security platform's CI interface.
- Define the Bind Plane Agent's host IP address and the agreed-upon Syslog port as the destination.
- Ensure the Syslog format is compatible with the parser (refer to relevant documentation if needed).
- Consult Bind Plane’s documentation for detailed configuration instructions.
- Deploy & Configure Bind Plane Agent:
- Install Docker on your chosen Linux host if not already present.
- Install the Bind Plane Agent software following the relevant documentation.
- Configure the Bind Plane Agent using its configuration files. This typically involves defining:
- Receivers: Specify the IP address and port where the agent should listen for incoming syslog messages from the security platform.
- Exporters: Configure the connection details for your Google SecOps instance, including credentials and the crucial log_type (e.g., ot_security_platform_cyberinsight) that will identify this data source in Google SecOps.
- Service: Define the pipeline that links the configured Receiver to the configured Exporter, specifying that logs arriving at the Receiver should be processed and sent via the Exporter.
- Run the Bind Plane Agent and verify its operational and communicating correctly with both the security platform (receiving logs) and Google SecOps (exporting logs).
- Refer to the official Bind Plane Agent and Google Security Operations documentation for detailed installation and configuration steps.
- Enable & Configure UDM Parsing (in Google SecOps):
- Google SecOps uses UDM Parsers to normalize raw data. A custom parser specifically for your security platform's alerts is required. Metron often develops these specific parsers.
- This parser needs to be deployed to your Google SecOps instance (Our team coordinates this process with the Google team).
- Once available, configure a Feed in Google SecOps. This Feed should be configured to apply the specific custom parser to the data arriving with the log_type you defined in your Bind Plane Agent Exporter (e.g., ot_security_platform_cyberinsight).
- Verify in Google SecOps Search that alerts are arriving with the correct log_type and being correctly parsed into UDM fields.
Use Cases
Integrating your security platform's IoT/OT alerts with Google SecOps provides several advantages:
- Centralized IoT/OT Security Monitoring: Gain a single pane of glass for all security events, including those specific to IoT/OT devices, within the familiar Google SecOps interface.
- Enhanced Threat Correlation: Correlate IoT/OT-specific vulnerabilities or anomalies detected by CI with other network, endpoint, or cloud logs to identify sophisticated, multi-stage attacks traversing IT and OT environments.
- Improved Incident Response: Streamline investigations involving IoT/OT devices by having all relevant alert data readily available, normalized in UDM, and linked to other enterprise security data within Google SecOps.
- Simplified Compliance & Reporting: Leverage Google SecOps' powerful reporting and analytics capabilities on normalized IoT/OT data to help meet compliance requirements related to critical infrastructure and device security.
Conclusion
Integrating your OT Security platform's CI alerts into Google SecOps SIEM via syslog forwarding and the use of a data mediator like Bind Plane Agent streamlines IoT/OT security monitoring.
By following the outlined steps, organizations can leverage the strengths of both platforms, enabling centralized visibility, enhanced correlation, and faster response to threats targeting their connected device infrastructure. The use of a custom UDM parser ensures the OT-specific context is correctly understood and utilized within Google SecOps.
Metron Security is a leading provider of custom-built and on-demand third-party integrations for security ecosystems and a trusted development partner for many top security companies, ranging from the fastest-growing to the largest enterprises. The team has worked on over 300 security applications and continues developing new ones monthly. Reach out to us at connect@metronlabs.com to learn more.









