Enhancing the Security of Wireless IoT Devices with the NAC platform and IoT Cloud Management Service Provider
In this case study, we explore how a large manufacturing company addressed the security concerns of their wireless IoT devices through integration.
Kshitij Kunte

Wireless IoT devices have become ubiquitous in industries ranging from healthcare to manufacturing to retail. However, effectively managing and securing these devices can be challenging, especially when they are deployed in large numbers. Furthermore, the increasing number of cyberattacks on IoT devices has highlighted the need for stronger security measures to protect them from unauthorized access and data breaches.
In this case study, we explore how a large manufacturing company addressed the security concerns of their wireless IoT devices by integrating the Aruba Wireless LAN Controllers (WLC) and IoT Cloud Management Service Provider. The integration involved applying Access Control Lists (ACLs) and Quarantine Policies to the wireless IoT devices through the NAC platform, fetching device details from the IoT Cloud management Service Provider, and monitoring the integration status to ensure the proper functioning of the system.
Background:
A large manufacturing company had deployed wireless IoT devices across multiple locations to improve their manufacturing processes. However, the company faced several challenges in securing these devices due to the lack of properly established security measures.
To manage the devices, the company was using NAC platforms, but there was a need to apply ACLs and Quarantine Policies to the devices to augment security. Additionally, there was no system in place to monitor the integration status of the NAC platform and the IoT Cloud Management Service Provider or to fetch device details from the IoT Cloud Management Service Provider.
Problem Description:
The challenge was to address the security concerns of their wireless IoT devices and to set up a system to monitor the integration status of the NAC platform and the IoT Cloud Management Service Provider.
The client's primary concerns were:
- Lack of proper security measures to protect IoT devices from cyberattacks;
- No system in place to monitor the integration status of the NAC platform and IoT Cloud Management Service Provider;
- No way to fetch device details from the IoT Cloud Management Service Provider.
Our team analyzed the client's requirements and recommended integrating the NAC platform and IoT Cloud Management Service Provider. By doing so, we could apply ACLs and Quarantine Policies to the devices for better security, fetch device details from the IoT Cloud Management Service Provider, and monitor the integration status of the NAC platform and the IoT Cloud Management Service Provider.
Integration Architecture:
- The integration architecture established a seamless data flow between the NAC platform and the IoT Cloud Management Service Provider through an API.
- The integration was enabled by a custom module created in XSOAR, a SOAR platform.
- The IoT Cloud Management Service Provider could trigger specific incidents in XSOAR, which were associated with corresponding playbooks designed to apply policies to the IoT devices.
- The playbooks would extract the required attributes related to the policies from the incidents and connect to the NAC platform through the API to apply the policies to the devices.
- To minimize the number of API calls, devices were batched when updating.
- The status of policy application was reported back to the IoT Cloud Management Service Provider through the API.
- Error minimization techniques were employed to ensure smooth and uninterrupted data flow.
- The integration architecture also included a system to monitor the integration status of the NAC platform and the IoT Cloud Management Service Provider in real-time.
- The monitoring system enabled quick identification and resolution of any issues.
To provide a visual representation of the integration architecture, the following diagram details this process:
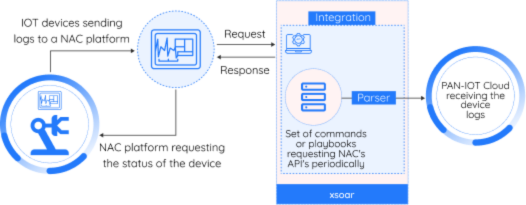
Polling:
The integration system periodically polled the NAC platform to gather client details, which were then reported to the IoT Cloud Management Service Provider through APIs. Any errors encountered during the polling process were also reported back to the IoT Cloud Management Service Provider via the API.
Batching:
To minimize the number of API calls made to the IoT Cloud Management Service Provider, the integration system employed batching of device updates.
Multiple commands:
The integration system utilized multiple commands to perform its functions, including creating ACL and quarantine incidents, reporting the integration status of the NAC platform and the IoT Cloud Management Service Provider, and gathering client details through polling.
Mappers:
To extract and map the required attributes related to the NAC platform and the policies to be applied to the devices, the integration system utilized mappers. These mappers extracted the necessary data from the incidents triggered by the IoT Cloud Management Service Provider and mapped them to the corresponding fields in the incident-specific playbook.
Classifiers:
To categorize the incidents based on their type (ACL or quarantine) and associate them with the incident-specific playbook, the integration system utilized classifiers. These classifiers ensured that the correct incident-specific playbook was triggered to apply the appropriate policy to the wireless IoT devices.
Integration Workflow:
- The integration between the NAC platform and the IoT Cloud Management Service Provider enables efficient management of wireless IoT devices and enhances device security. The integration process involves creating a module in XSOAR that communicates with both the NAC platform and the IoT Cloud Management Service Provider.
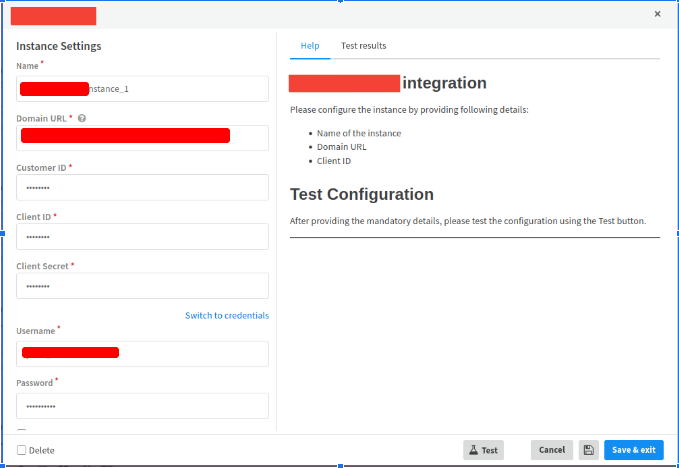
- An instance of the integration is created in XSOAR which is then configured with details of the IoT Cloud Management Service Provider and the NAC platforms details. A test connection request is made to check the connectivity from XSOAR.
- The prime purpose of the integration is to enable seamless data flow between the two systems. Whenever a device-related event occurs, such as a device being added, deleted, or modified, it triggers an incident in XSOAR. The incident contains device-related data and is associated with a playbook.
- The playbook extracts the required attributes related to the incident and connects to the NAC platform and IoT Cloud Management Service Provider through APIs. The playbook collects device-related data and batches it together before sending it to the IoT Cloud Management Service platform to minimize the number of API calls as
5. Once the playbook receives the device-related data, it applies the appropriate policies to the devices, such as access control lists and quarantines, depending on the nature of the incident. It then reports the status of the policy application back to the IoT Cloud Management Service Provider through the API.
6. To ensure smooth and uninterrupted data flow between the two systems, the playbook is designed to handle errors and exceptions gracefully. The playbook ensures that the policies are applied correctly and that the integration system is functioning correctly.
7. In addition, the integration system periodically polls the NAC platform to report client details to the IoT Cloud Management Service Provider and to check for any errors in connecting to the NAC platform. This ensures that the integration status is continuously monitored in real-time, enabling quick identification and resolution of any issues.
Overall, the integration between NAC platform and IoT Cloud Management Service Provider provides an efficient way to manage wireless IoT devices, enhance device security, and ensure seamless data flow between the two systems.
Playbooks:
The incident-specific playbooks were designed to automate the process of applying ACL and Quarantine policies to the wireless IoT devices through the NAC platform. These playbooks extracted the required attributes related to the policies from the incidents triggered by the IoT Cloud Management Service Provider and mapped them to the corresponding fields in the NAC platform. The playbooks also classified the incidents based on their type (ACL or quarantine) and associated them with the appropriate policy application commands.
The “Get Client Attributes Details” playbook involved the following steps:
- Connect to one or more NAC platforms configured for the Integration instance;
- For each NAC platform, get a list of access points and the list of client devices connected to access points from the NAC platform;
- For each client device, get client details from NAC platform are described in the table below;
- Report the client attributes details back to the IoT Cloud Management Service Provider through the API.
| Field | Description |
|---|---|
| Client Details | Details about the client device. |
| MAC Address | Media Access Control (MAC) address of the client. |
| IP Address | IP address of the client device. |
| Radio | Wireless radio used by the client device. |
| Status | Connection status of the client device. |
| AP Name | Name of the Access Point (AP) to which the client device is connected. |
| WLAN ID | WLAN ID of the wireless network to which the client device is connected. |
| SSID | Name of the wireless network to which the client device is connected. |
| Authentication Status | Authentication status of the client device. |
| Duration of Connection | Length of time the client device has been connected to the AP. |
| RSSI | Received Signal Strength Indicator (RSSI) of the client device. |
| SNR | Signal-to-Noise Ratio (SNR) of the client device. |
| AP Radio Slot Id | Slot ID of the AP radio to which the client device is connected. |
| Port | Port used by the AP radio to which the client device is connected. |
| Access Point Details | Details about the Access Point to which the client device is connected. |
| AP Name | Name of the Access Point (AP) to which the client device is connected. |
| AP Model | Model of the Access Point to which the client device is connected. |
| Number of Slots | Number of slots available on the AP. |
| Ethernet MAC Address | MAC address of the Ethernet port of the AP. |
| IP Address | IP address of the AP. |
| Location | Physical location of the AP. |
| Country | Country where the AP is located. |
| Total Clients | Total number of client devices connected to the AP. |
| Authentication | Authentication method used by the AP. |
| Authentication Algorithm | Algorithm used for authentication. |
| Encryption Cipher | Encryption cipher used by the AP. |
| Bluetooth Client Details | Details about the Bluetooth client device (TBD). |
| Bluetooth MAC Address | MAC address of the Bluetooth client device. |
| Discovery Type | Type of Bluetooth discovery (e.g. BLE beacon, BT-discovery, BT-link). |
The ACL playbook:
- The playbook receives an incident from the IoT Cloud Management Service Provider that triggers an ACL policy application to a specific IoT device.
- The playbook extracts the required attributes related to the ACL policy, such as the device IP address, the policy name, and the action (allow/deny), from the incident.
- The playbook maps the extracted attributes to the corresponding fields in the NAC platform and creates an ACL incident to apply the policy.
- The playbook sends the policy application command to the NAC platform and waits for the response.
- If the policy is successfully applied, the playbook reports the policy application status back to the IoT Cloud Management Service Provider through the API. If the policy application fails, the playbook generates an error message and reports the failure to the appropriate personnel.
The Quarantine playbook:
- The playbook receives an incident from the IoT Cloud Management Service Provider that triggers a Quarantine policy application to a specific IoT device.
- The playbook extracts the required attributes related to the Quarantine policy, such as the device MAC address, the policy name, and the action (quarantine/release), from the incident.
- The playbook maps the extracted attributes to the corresponding fields in the NAC platform and creates a Quarantine incident to apply the policy.
- The playbook sends the policy application command to the NAC platform and waits for the response.
- If the policy is successfully applied, the playbook reports the policy application status back to the IoT Cloud Management Service Provider through the API. If the policy application fails, the playbook generates an error message and reports the failure to the appropriate personnel.
An example of the quarantine playbook is given below:
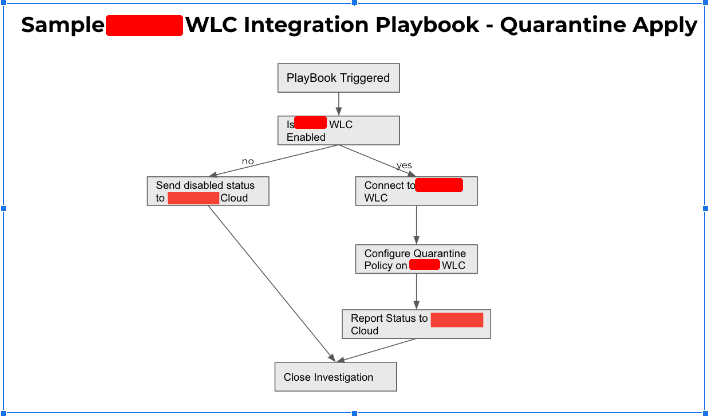
The playbooks were designed to be scalable and to handle a large number of incidents simultaneously. They were also configured to handle errors and exceptions, ensuring that the policies were applied correctly and that the integration system was functioning properly.
Overall, the integration of the NAC platform and the IoT Cloud Management Service Provider provided the client with an effective and automated solution to enhance the security of its wireless IoT devices. The integration system streamlined the process of applying ACL and Quarantine policies to the devices and provided a system to monitor the integration status of the NAC platform and the IoT Cloud Management Service Provider.
Benefits:
- Enhanced Security: By applying ACLs and Quarantine Policies to the wireless IoT devices, the integration provided an added layer of security to the client's network. The ACLs enabled the client to restrict network access to specific devices or groups of devices, based on attributes such as device type, IP address, MAC address, and more. This helped prevent unauthorized access and data breaches, as well as mitigate the risks associated with compromised devices.
- Efficient Management: The integration provided an efficient way to manage the wireless IoT devices across multiple locations, by enabling the client to centrally manage and apply policies to the devices. The policies could be customized and applied to specific devices or groups of devices, based on various attributes, such as device type, location, and more. This simplified the management of the devices and ensured consistent policy enforcement across the network.
- Real-time Monitoring: The integration system provided real-time monitoring of the integration status of the NAC platform and the IoT Cloud Management Service Provider, which enabled the client to quickly identify and resolve any issues. The monitoring system provided alerts and notifications in case of any issues, such as failed policy applications, network connectivity issues, and more. This helped ensure that the integration system was functioning correctly and that the policies were being applied as intended.
| Activity | Timeline |
|---|---|
| Requirements Gathering & Integration Design | 1 week |
| Development and Testing | 2 weeks |
| User Acceptance Testing | 1 week |
| Total | 4 weeks |
Project Timelines:
The project timeline for integrating NAC platform with XSOAR can be divided into two phases:
Phase 1: Planning and Setup
Phase 2: Deployment and Optimization
| Activity | Timeline |
|---|---|
| Deployment and Configuration | 1 week |
| Optimization and Fine-Tuning 2 | 1 week |
| Development and Testing | 1 week |
| Documentation and Publishing | 1 week |
| Total | 4 weeks |
Deliverables:
The deliverables for this project include:
- Integration of the NAC platform with XSOAR
- Configuration polling intervals for retrieving data from the NAC platform
- Mapping Aruba WLC data to XSOAR using mappers
- Classifying events generated by the integration using classifiers
- Playbooks for automating network management tasks, troubleshooting network issues, and responding to security incidents
Major Components:
The major components of the integration include:
- NAC platform
- XSOAR
- REST API client for communication between NAC platform and XSOAR
- Polling for retrieving data from NAC platform
- Mappers for mapping data from NAC platform to XSOAR
- Classifiers for categorizing events generated by the integration
- Playbooks for automating network management tasks, troubleshooting network issues, and responding to security incidents
Publishing the App:
The integration can be packaged as an XSOAR app and published to the XSOAR app marketplace. The app can be made available to XSOAR customers who use the NAC platform in their wireless networks. The app can also be customized to meet specific customer requirements by modifying the mapping table, classifiers, and playbooks.
Conclusion:
The integration of the NAC platform and the IoT Cloud Management Service Provider provided a robust solution for enhancing the security of wireless IoT devices deployed across multiple locations. The integration allowed for the efficient management of the devices and provided real-time monitoring of the integration status. The client was able to enhance the security of their devices and protect them from cyberattacks, making their manufacturing process more secure and efficient.
About Metron:
Metron is a trusted provider of on-demand and effective approaches to managing third-party integrations for security ecosystems. With extensive experience in delivering automation solutions for over 200 security applications, Metron has earned the trust of numerous fast-growing security companies and managed security service providers (MSSPs).
Metron’s transparent development processes, deep understanding of security products, and fixed-cost model have resulted in shorter development times and significant cost savings for clients compared to deploying internal engineering teams for similar tasks. Headquartered in Novato, CA, with development offices in Bangalore and Pune, India.
Connect with Metron at connect@metronlabs.com.









