Improved Data Integration with OCSF
Discover how OCSF helps break down data silos and streamlines inter-application communication.
Anmol Jain

The cybersecurity world has consistently struggled with scattered data which has led to hindered threat detection and response. Security tools from different companies often operate in silos, using unique formats that only their own apps understand. This creates communication roadblocks and makes it difficult to gain a comprehensive view of your security posture.
Fortunately, the Open Cybersecurity Schema Framework (OCSF) – a standardization framework - aims to break down these silos and streamline the process through which integrated applications can communicate with one another.
In the following article, we’ll outline how this process works along with some of the key benefits.
Note, we’ve previously discussed the data-standardizing schema of OCSF. Please review that article for further details.
Enabling Seamless Data Integration
OCSF is intended to act as a universal adapter for security data. It defines common formats for different security events and components, among them: users, devices, and vulnerabilities. This eliminates the need for complex data conversions between your integrated tools, allowing security systems to easily understand and use data from various sources.
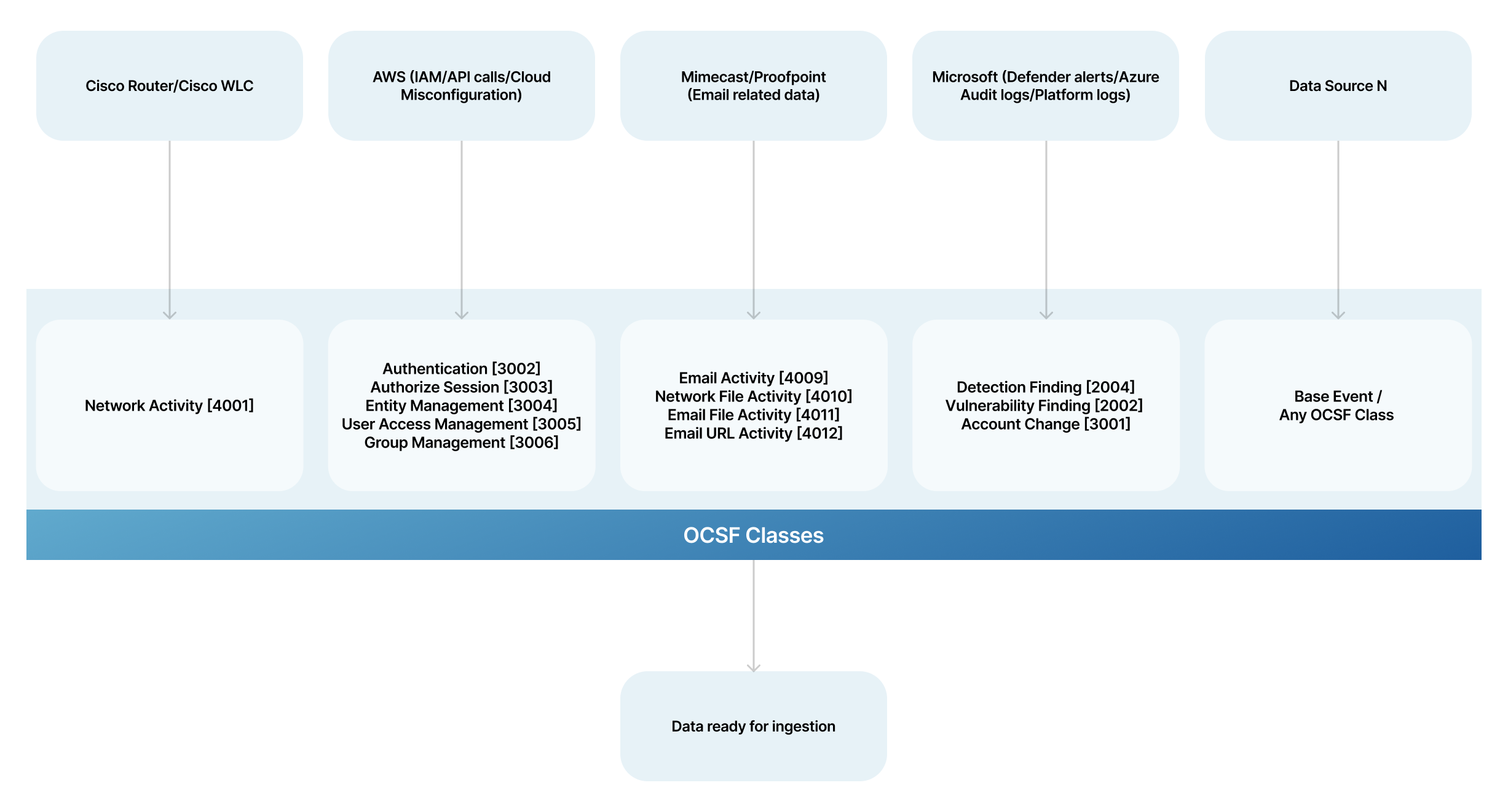
Here's how OCSF makes data integration smoother:
- Shared Language (Schema): OCSF defines a shared language, a blueprint that dictates how security data should be structured and formatted. This blueprint specifies the data points (e.g., time, severity, duration) and their expected formats (e.g., timestamp, string, integer). Security tools that follow OCSF can easily understand and interpret data from each other, regardless of the source.
- Reduced Mapping Hassles: Traditionally, security teams rely on custom tools or scripts to translate data from various formats into a single format for analysis. This process can be complex, error-prone, and time-consuming. OCSF eliminates this need by providing a pre-defined language, streamlining data integration efforts. Security tools that support OCSF can directly take in and process data without complicated mapping configurations.
- Enhanced Interoperability: OCSF promotes interoperability between security tools from different vendors. By adhering to a common schema, security products can share data seamlessly, fostering a more open and collaborative security ecosystem. This allows security teams to leverage best-of-breed solutions from various vendors without worrying about data compatibility issues.
Standardized Data Exchange for Integrated Security with OCSF
OCSF lays the groundwork for better data integration, but it's just the beginning. Here are advanced strategies to leverage OCSF for a more comprehensive security approach:
Centralized Logging Hub
Implement a central logging platform that can ingest data from various security tools in OCSF format. This central repository allows for unified log analysis, threat hunting, and incident investigation. Security analysts can easily connect events across different systems using standardized data fields, leading to faster identification of potential threats.
Security Data Lake
Consider building a security data lake specifically designed to store all security-related data in its native OCSF format. This data lake acts as a centralized data repository, enabling advanced security analytics and machine learning for threat detection.
Standardized schemas in OCSF not only facilitate seamless data ingestion and analysis within the data lake but also create high-quality data for machine learning. Because OCSF predefines data formats and eliminates the need for complex transformations, security teams can spend less time on data understanding, data preprocessing, and cleaning steps. This allows them to focus on building and deploying powerful threat detection algorithms that leverage the rich data available in the security data lake.
Automation and Workflows
OCSF can be a powerful tool for automating security workflows. By leveraging standardized data formats, security events can trigger automated responses based on predefined rules within the central logging platform or security data lake. This allows for faster and more efficient incident response, minimizing the impact of potential attacks.
The Future of Security with Integrated Data
OCSF marks a significant step towards a future where security systems seamlessly communicate and share data. This fosters a more collaborative and comprehensive security approach, enabling organizations to:
- Proactive Threat Hunting: With data from various sources readily available in a standardized format, security teams can proactively hunt for threats. By correlating events across different security tools, they can identify suspicious activity and potential attack patterns before they escalate into major incidents.
- Improved Security Posture: OCSF empowers security teams to gain a complete understanding of their overall security posture. By analyzing integrated data across the entire security ecosystem, they can identify security gaps and vulnerabilities, allowing for targeted mitigation strategies.
- Reduced Response Times: Integrated data provides a clear picture of the threat landscape, enabling security teams to respond to incidents faster and more effectively. With standardized data readily available, they can quickly assess the scope and severity of an incident, taking appropriate action to contain the threat and minimize damage.
Embracing OCSF
OCSF acts as a roadmap for improved data integration within security environments. By adopting OCSF and implementing the strategies outlined above, security teams can unlock the true potential of their security investments.
If you are looking to set up any integrations with the OCSF Schema and are facing challenges, you can contact us at connect@metronlabs.com. Metron is a contributor to the OCSF framework and a trusted development partner for many of the industry’s leading providers.









