Integrating Your Digital Risk Protection (DRP) Platform with Microsoft Sentinel
Sentinel can act as your organization's security control tower when paired with a Digital Risk Platform (DRP). Learn how!
Anmol Jain

Ever wondered how security teams manage to keep track of thousands of alerts across their organization's entire digital footprint? It’s not easy, especially when their digital ecosystem spans clouds, data centers, and countless devices.
Fortunately, apps like Microsoft Sentinel can facilitate this process. Combining the capabilities of a cloud native SIEM with a SOAR, when well-integrated, this security powerhouse doesn't just collect data but actually makes sense of it using AI and machine learning.
So, whether you're dealing with Microsoft 365 alerts, third-party security tools, or an old legacy system that nobody really wants to talk about, Sentinel can act as your organization's security control tower - giving you that big-picture view while automatically handling the routine tasks.
Architecture of Microsoft Sentinel
The Foundation: Core Infrastructure
Microsoft Sentinel runs on Azure, so you need an active Azure subscription to get started.
Sentinel also uses a Log Analytics workspace to store all your security data.
Here's a tip: always use a dedicated workspace for Sentinel. Why? Because alert rules and investigations don't work too well across multiple workspaces.
Key Components: The Middle
Visualization & Investigation Tools
First up, we have dashboards and workbooks. Think of these as your security command center. The built-in dashboards give you instant visibility into your connected data sources, while custom workbooks let you slice and dice the data your way.
Need to investigate something suspicious? That's where cases and incidents come in. They bundle related alerts together, making it easier to track investigations and delegate tasks to your team.
Proactive Hunting & Analysis
The hunting capabilities in Sentinel are where things get interesting. Powered by Kusto Query Language (KQL), you can write custom queries to hunt for threats proactively.
Automation & Response
Nobody wants to manually respond to every alert. That's why Sentinel includes playbooks built on Azure Logic Apps. These automated workflows can trigger responses as soon as an alert fires.
Data Integration
A SIEM is only as good as its data sources, and Sentinel offers multiple ways to ingest data:
- Service-to-Service connections for Microsoft products
- API integrations for third-party solutions
- Agent-based collection for Syslog and CEF logs
Analytics: The Top Layer
At its core, Sentinel's analytics engine helps you make sense of all this data. Using KQL, you can create custom alert rules or use pre-built ones. These analytics can trigger incidents or kick off automated responses through playbooks.
Integrating Microsoft Sentinel with Digital Risk Protection Platform
Why Integrate Your DRP Platform with Microsoft Sentinel?
- Unified Threat Visibility:
Combine external threat intelligence from your DRP platform with internal security data in Microsoft Sentinel for a comprehensive view of your entire threat landscape.
- Automated Cross-Platform Response:
Trigger automated responses to external threats detected by your DRP platform through Microsoft Sentinel's playbooks, reducing response times and human error.
- Enhanced Threat Correlation:
Identify sophisticated attack patterns by correlating external threat indicators from your DRP platform with internal events monitored by Microsoft Sentinel.
- Streamlined Security Operations:
Reduce context switching between platforms by centralizing alerts and incidents in a single pane of glass, improving analyst efficiency.
- Scalable Threat Management:
Handle increasing volumes of security data from both internal and external sources with Microsoft Sentinel's cloud-native architecture.
- Improved Incident Prioritization:
Accurately prioritize security incidents by enriching Microsoft Sentinel alerts with external threat context from your DRP platform.
Microsoft Sentinel Integration Architecture
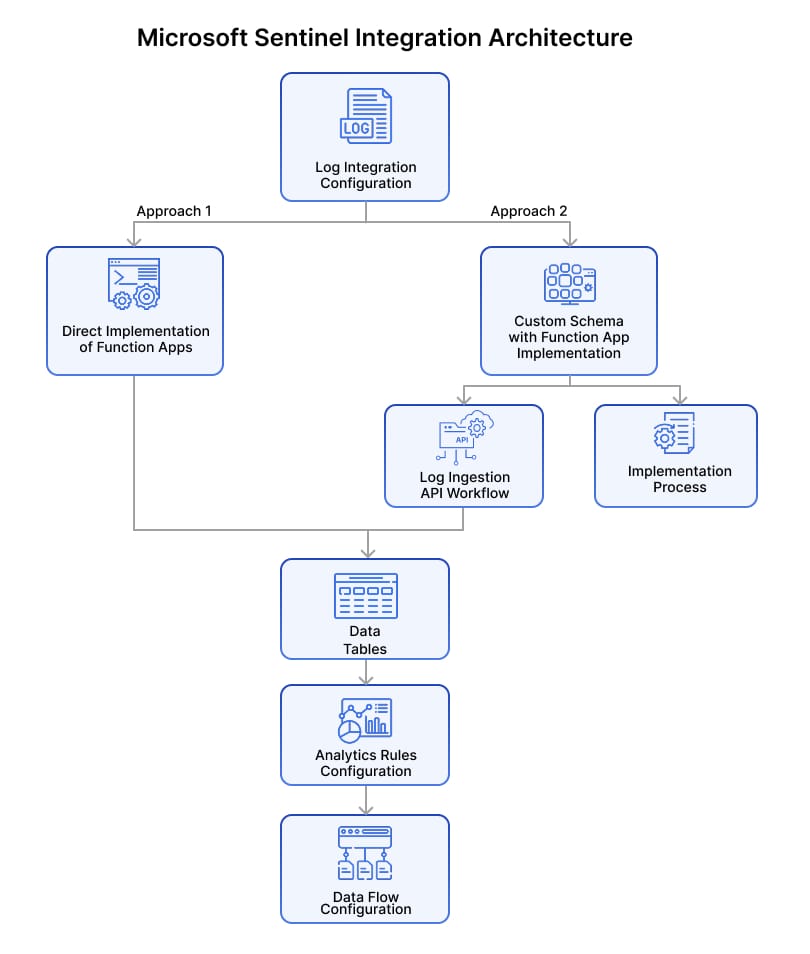
Step 1: Log Integration Configuration
The first crucial step is establishing a robust connection for log transmission from your DRP platform to Microsoft Sentinel. You have two primary approaches to accomplish this:
Approach 1: Direct Implementation of Function Apps
Function Apps serve as a serverless computing service that allows you to run code without managing infrastructure. When implementing this approach, the data received by the function app is typically unstructured. The process involves:
- Create an Azure Function App in your Azure portal.
- Configure the necessary authentication and connection settings for the function app to receive data.
- Develop the function code to handle the transformation of the initially unstructured log data into a structured format suitable for Microsoft Sentinel, followed by its transmission.
- Test the connection to ensure proper data flow and the successful structuring of data within the function app.
Approach 2: Custom Schema with Function App Implementation
This approach creates a tailored data structure that maps your DRP platform's log format to Microsoft Sentinel's requirements. The data is structured according to your defined custom schema, with a function app handling any further processing or transmission needs.
Implementation Process
- Analyze Log Structure: Thoroughly examine your existing DRP log format to understand all components and data relationships.
- Design Compatible Schema: Create a schema that aligns with Sentinel's data model while accommodating your specific logging requirements.
- Implement Mapping Logic: Develop transformation processes to convert your DRP platform logs into the defined custom schema.
- Validate Transformations: Test and verify that logs are correctly structured according to your custom schema before function app processing.
Log Ingestion API Workflow
The data was previously sent to the Function App directly via HTTP Data Collector API, and the data was stored in a custom table. The new Log Ingestion API follows this streamlined process for data transmission:
- Authentication Setup: App registration and secret key creation (handled automatically by Sentinel's framework)
- Schema Definition: Create your table schema with all required fields and data types
- Rule Configuration: Define data collection rules, including mapping and transformation specifications
- Transmission: Use Data Collection Endpoints/Rules (DCE/DCR) to send the data through the Log Ingestion API
Note: Microsoft Sentinel will deprecate the feature to send unstructured data directly via HTTP Data Collector API by 2026. Planning your migration to structured data ingestion now will ensure continued compatibility.
Step 2: Analytics Rules Configuration
Once the log integration is established, setting up analytical rules is essential for automated threat detection and response. You need to set rules with queries using KQL (Kusto Query Language)
These rules act as continuous monitors of your incoming log data and trigger specific actions based on predefined conditions.
Key Actions That Can Be Triggered:
1. Incident and Alert Creation
When configuring incident creation:
- Define severity levels
- Set alert categorization
- Establish notification parameters
- Configure incident details templates
2. Playbook Execution
Playbooks automate your response workflows:
- Design response sequences
- Set triggering conditions
- Configure action parameters
- Establish execution priorities
3. Incident Assignment
Automated assignment ensures rapid response:
- Define assignment rules
- Set up escalation paths
- Configure team notifications
- Establish SLA parameters
Data Flow Configuration
An important consideration in this integration is the direction of data flow. You can configure this based on your specific requirements:
Unidirectional Flow
- Data moves only from your DRP platform to Microsoft Sentinel
- Suitable for organizations requiring simple log aggregation
- Maintains stricter data boundaries
Bidirectional Flow
- Enables two-way communication between systems
- Allows for more complex automation scenarios
- Facilitates comprehensive security orchestration
Conclusion
Whether you're a small team looking to automate security monitoring or a large enterprise requiring threat detection, Microsoft Sentinel's architecture provides the flexibility to meet your needs. The combination of built-in intelligence, automation capabilities, and community support makes it a compelling choice for organizations looking to modernize their security operations.
Is your organization looking to set up any integrations with Microsoft suite products or having trouble connecting security apps with its infrastructure? For any queries or integration needs of your business, concerning cybersecurity platforms, please feel free to reach out to us at connect@metronlabs.com.









