Metron Security’s Dev-Centric Code Jam: Here’s A Glimpse of What Went Down
Metron Code Jam January 2025: A thrilling fusion of coding, collaboration, and cybersecurity innovation!
Akanksha Kumari
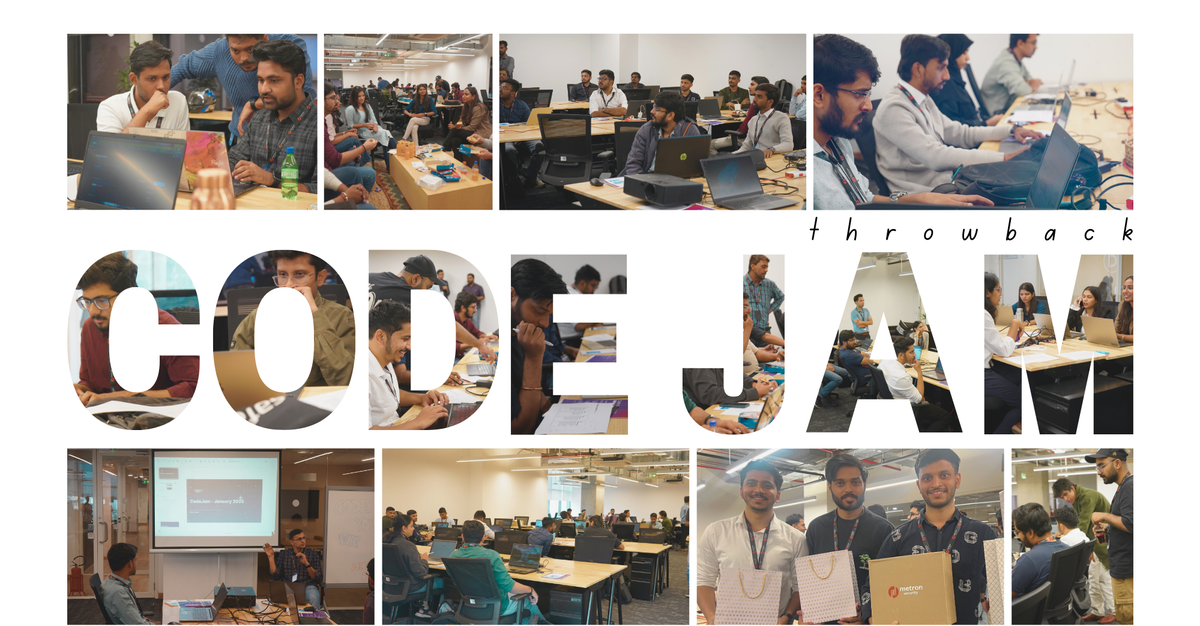
The stakes were high, and the clock was ticking. At 3:00 PM, developers from across Pune gathered for the 6-Hour Code Jam: Elastic SOC Edition. This wasn’t just about writing code; it was a race against time and a celebration of creativity, problem-solving, and innovation in cybersecurity.
At Metron Security, we’re all about sparking innovation and creativity in the world of cybersecurity, and the Metron Code Jam Jan 2025 was a true testament to that mission! With passionate coders, cybersecurity enthusiasts, and brilliant problem-solving minds coming together, this event was electric. If you were there, you already know the magic we created. If not, don’t worry (we have more such events in store for you)—here’s a sneak peek into what went down and what’s coming up next!
Event Details
Inaugural Code Jam (First of many) Date: 16th January 2025 Location: WeWork, Baner, Pune Organizer: Metron Security
The Metron Code Jam - A SOC Dev Jam wasn’t just a typical coding event—it was a chance to dive into the heart of Security Operations Center (SOC) challenges, tackle real-world cybersecurity problems, and ignite fresh ideas that push the boundaries of what’s possible.
Purpose of the Event
The ultimate goal of this Metron CodeSOC Dev Jam was to bring together a diverse group of coding enthusiasts and cybersecurity problem-solvers. We wanted to challenge participants with real-world cybersecurity problems that require fresh, creative thinking. This event wasn’t just about solving problems—it was about doing so in a way that leaves an impact. We aimed to fuel collaboration, inspire creativity, and foster innovation in the cybersecurity community.
The Kickoff
The event kicked off with a quick briefing from Parag Patwardhan, Chief Architect, who introduced the problem statement and set the stage for the evening. The first step in setting up a SOC is to ingest data, logs, and events from multiple cybersecurity tools. For this CodeJam, we selected a few security tools that would be commonly used in a company. We also allowed people to roll out their own, simplified version of a file monitoring tool that would create an alert when malicious files were detected. All of these events had to be pushed to a central Elastic server that we had set up for the CodeJam.
Over 30 participants came together and got to work with a variety of technologies and building blocks—APIs, data streams, and dashboards, in whichever languages they preferred. Whether they were Elastic Stack veterans or newcomers, the community spirit was undeniable. With questions, tips, and solutions flying across the room, the atmosphere was buzzing with collaboration.
The First Hour: Setting the Foundation
The opening hour was all about laying the groundwork. Individuals dove into configuring their infrastructure and they started off with:
- Sorting out access to Elastic, to ensure that they had the right permissions required to push events.
- Researching the API documentation for Elastic and ensuring that they can push sample events to the index.
- Experimenting with Kibana for quick visualizations
Our team of developers and engineers played a significant role here. They made sure that no one was stuck and if they were, they had the help that nudged them towards the right direction. Some of the tips they shared are mentioned below:
Tip 1: APIs and authentication
The first tip was to make sure that you can authenticate with the Elastic API server using the documented authentication methods.
Once you are able to push sample events into Elastic, you know that you have a solid foundation to build the rest of the project.
Tip 2: Setup your development environment
Participants were allowed to use any language, framework, IDE, etc that they were comfortable with. The intent was to rapidly get started with the development process, instead of trying to force people into any particular stack.
The Midway Grind: Problem-Solving Mode
By hour three, the energy in the room was palpable. The participants were troubleshooting, refining their setups, and collaborating with their peers.
Tip 3: Bulk Upload
Participants figured out how to use the Bulk Upload API to push batches of events to Elastic. This allows for a large number of events to be pushed to the server with a minimal number of API calls.
As the coding marathon continued, pizza and snacks were brought in to fuel and keep everyone going, adding a touch of humor and camaraderie to the intense competition, and giving them time to mingle with their peers and our team members. After all, nothing brings developers together like a slice of pizza and a shared laugh over debugging.
The Final Hour: Crunch Time
As the clock ticked, the final hour arrived in a whirlwind of activity. Participants were fine-tuning their code, adding custom Kibana visualizations, and configuring alerts to ensure the SOC (Security Operations Center) could react in real time.
Tip 4: Dashboards
The volume of security data makes it hard for SOC analysts to sift through. Having pre-configured dashboards of the data that you ingested makes it easier to find the proverbial security needle in the haystack!
The real proof of the CodeJam is always in the code. Participants scrambled to polish their demos so that they could show the system working in real time. The energy was high, but so was the excitement!
Showtime: Demos and Applause
After hours of intense work, it was time to showcase the solutions. The code packages were reviewed, discussions took place between the judges, and then came the moment of truth. From one-liner integrations to innovative dashboards and multi-tool systems, the judges were impressed by the creativity and execution under immense time pressure.
The Winning Moment
After some intense deliberation, we had 3 individuals who emerged victorious, with Prathamesh Vagare holding the first position, Parth Rajeshwar Komalwad holding the second, and Gourav M. Kadu being our first runner-up. Their integration of Elastic’s Machine Learning capabilities paired with an elegant and user-friendly dashboard, was unmatched. As Kapil, Director of Engineering and one of the judges aptly put it:
"The way certain participants integrated ML and visualization to identify threats in real-time was a standout. It was an outstanding solution executed under immense time pressure."
Apart from the three, there were also a few others who took the problem presented to them at hand and came to us with great solutions.
Developer Lessons and High Fives
By the end of the event, participants walked away with more than just a sense of achievement:
- A deeper understanding of the Elastic Stack’s potential.
- New connections with like-minded developers.
- A treasure trove of reusable code and ideas.
One of the candidates summed it up best: "I came in thinking Elastic was just a logging tool. Now, I see it’s a whole ecosystem."
Announcement: Next Code Jam
Now, for the exciting part—our next event, Code Jam Feb 2025 is just around the corner, and we’re ready to bring even more excitement, innovation, and challenges your way.
Save the Date:
Date of the Event: 22nd February 2025 Location: WeWork, Baner, Pune Last registration date: 20th February 2025
We’re already gearing up for the next round of challenges, and trust us, it’s going to be bigger, better, and more exciting than the last one. Expect new challenges, awesome rewards, and of course, the chance to make your mark in the field of cybersecurity.
Let’s Do It Again!
Don’t miss out on the next challenge! Register by 20th February 2025 for a chance to innovate and shine in the world of cybersecurity.
Thank you to all participants and the incredible Metron team for making this event a success. We can’t wait to see more of the developer community at our next Code Jam!










