ServiceNow SecOps Architecture: From Detection to Response
Integrate your security stack with ServiceNow SecOps to streamline detection, automate response, and gain unified visibility across incidents, threats, and IT operations.
Neel Bafna

Organizations often face an overflow of alerts, vulnerabilities, and risks from various tools/systems.
If this sounds familiar, you’ve likely asked yourself the question: how do you respond, prioritize, and solve these alerts before they affect your security stack?
The answer is relatively straightforward and lies in integrating your platform with a tool like ServiceNow’s Security Operations (SecOps).
ServiceNow SecOps unites processes and technology to protect your organization against evolving threats and respond swiftly to attacks. Once connected, this integration can act as the central nervous system for security and IT operations.
In this blog, we will guide you through the ServiceNow SecOps platform and demonstrate how it can enable seamless workflows from detection to response.
ServiceNow SecOps and its Features: The Central Nervous System of Security and IT Operations
The strength of any security platform lies not necessarily in its ability to detect threats, but more so in how effectively it reacts to them.
Previously, businesses relied on SIEM platforms for monitoring, scanners for vulnerability detection, and threat feeds for intelligence. But without a structured, integrated architecture with other security platforms, these tools aren’t that useful.
ServiceNow SecOps can provide this structured architecture when it’s integrated with your wider security stack. More importantly, ServiceNow SecOps offers a range of powerful features that will help you strengthen workflows, automate responses, and achieve real-time visibility across your security landscape.
Among them:
- Security Incident Response (SIR): By integrating your security tools with ServiceNow SIR, you can ensure that alerts are associated with incidents that can be taken action on. This eliminates duplication, lessens alert fatigue.
- Vulnerability Response (VR): You may consolidate findings, rank remediation, and link vulnerabilities to Configuration Items (CIs) in the CMDB by integrating vulnerability scanners with ServiceNow. This guarantees that team members can concentrate on resolving the most important problems.
- Threat Intelligence Security Center: ServiceNow adds contextual threat data to incidents when your platform's intelligence feeds are linked. This speeds up decision-making by assisting the right team members in rapidly assessing the seriousness and extent of threats.
- Configuration Compliance: You may continuously evaluate whether systems and apps adhere to security policies and legal requirements by integrating with ServiceNow. Automatic flagging of non-compliant setups enables quicker resolutions.
- Performance Analytics for Security Operations: Performance Analytics, one of the most useful tools, gives security directors access to real-time dashboards, KPIs, and predictive intelligence. Integrating your data allows for robust trend analysis and reporting that optimizes resource allocation and security posture.
- Data Loss Prevention (DLP) Incident Response: Creating and monitoring DLP incidents is automated if your platform generates DLP alerts and you input them into ServiceNow. This guarantees that sensitive data exposures are promptly contained and looked into in a methodical manner.
- Scalability and Flexibility: Scales to accommodate increasing data volumes without incurring additional operational costs and integrates seamlessly with existing security ecosystems.
These are the features and reasons why your cybersecurity platform should be integrated with ServiceNow SecOps. Now, let's dive deeper into ServiceNow SecOps and the platforms that can be integrated with its architecture.
ServiceNow SecOps Integration Architecture
More likely than not, your organization has SIEM, XDR, or other security tools helping fetch logs and alerts. The next step is making these actionable.
Integrating your security platform with the ServiceNow security stack, including ServiceNow SecOps, will not only allow your team to have a more detailed understanding of your organization’s security posture but also take necessary actions to secure your systems.
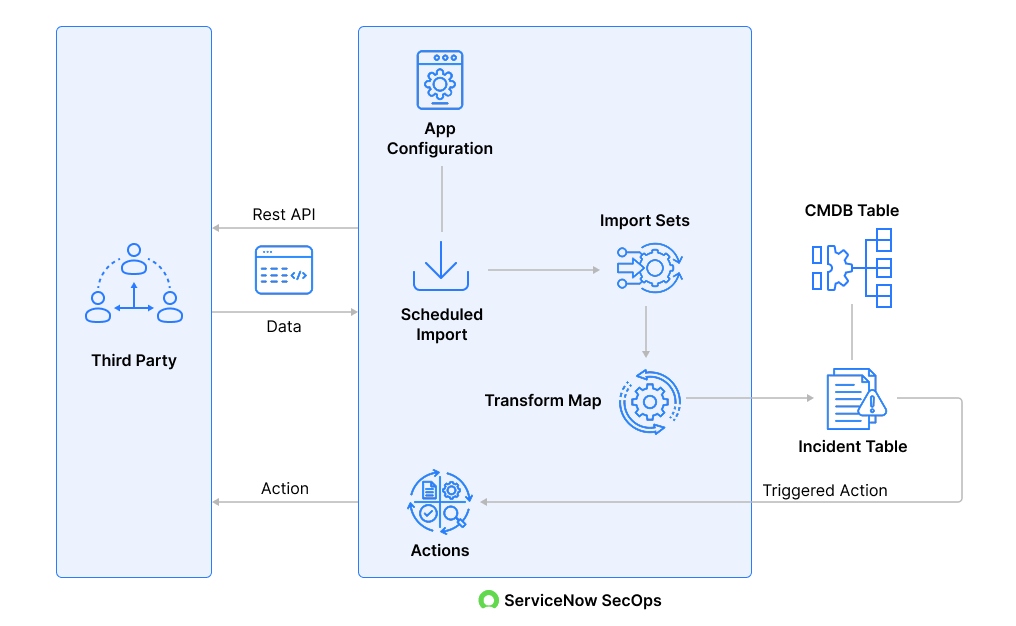
To take advantage of this, consider the following steps:
Step 1: Threat Source Integration and Configuration
To start with, set up plugins so that your platforms, whether SIEM, EDR/XDR, vulnerability scanner, or threat intelligence feed, can communicate directly with the ServiceNow platform. This integration ensures critical security incidents are shared continuously.
Step 2: Data Sharing via APIs
Enable REST APIs or connectors on your platform so that ServiceNow can fetch relevant data. You can also send real-time data directly to ServiceNow via APIs or push notifications for quick response.
Step 3: Scheduling Data Imports
Determine how frequently your platform wants to send or allow ServiceNow to pull data. This can be done every few minutes or based on the last API call.
These schedules are used by ServiceNow to retrieve the events and alerts from your platform. Your platform can also push data directly over webhooks or REST APIs for urgent or real-time events, bypassing scheduled pulls and providing immediate visibility.
Step 4: Data Storage in Import Sets
When data is sent to ServiceNow, it is first stored in Import Sets. For ServiceNow to read and understand your data, it uses Transform Maps to transform and normalize your data and stores it in its Incident table.
Step 5: Data normalization and Correlation
For exact correlation in ServiceNow SecOps, your platform must provide clean, non-duplicated, and standardized data.
Even if duplicate records exist at the source, ServiceNow’s Transform Map can automatically de-duplicate them using a unique identifier provided to your platform. This allows ServiceNow SecOps to normalize the inputs and merge related alerts into a single actionable security incident, preventing any duplication.
Step 6: Incident Creation and Response Coordination
Once data from your platform reaches ServiceNow, it contributes to the creation of incidents in the Security Incident Table.
Automated workflows can then take over, enabling actions such as blocking malicious IP addresses, disabling compromised accounts, or isolating affected systems. That will be completely based on the triggers generated from your alerts.
Step 7: Leveraging ITSM and CMDB Data
Whenever an incident requires IT intervention, ServiceNow automatically creates Change, Incident, or Problem tickets in ITSM. These are linked to Configuration Items (CI) in the ServiceNow Configuration Management Database (CMDB).
The CMDB shows how your assets are interconnected, while the CI link is useful for understanding which assets may be affected when taking any action to resolve an incident.
Step 8: Reporting and Continuous Improvement
By ensuring your platform shares complete and examined data, ServiceNow SecOps can also generate detailed dashboards and reports.
Over time, this information is used to fine-tune detection methods and response playbooks, improving both your platform’s and ServiceNow’s overall effectiveness in managing security incidents.
For example, in your organization, multiple users report a suspicious phishing email, ServiceNow SecOps can automatically block the sender domain across the organization, segregate the malicious emails from inboxes, and force a password reset for impacted users. By leveraging integrated threat intelligence, the system can also identify similar future attacks.
Conclusion
The step-by-step architecture above provides a detailed understanding of how ServiceNow SecOps integration effectively manages and handles data exchange between different third-party platforms.
As cyber threats become increasingly evident, businesses can no longer rely on manual processes. They need a platform that not only identifies threats but also ensures coordinated, automated, and business-aware responses.
ServiceNow SecOps delivers exactly that. By integrating with existing detection tools, enriching alerts with intelligence, orchestrating workflows, and embedding IT governance, businesses can transition from reactive firefighting to proactive security operations.
Is your organization looking to set up any integrations with ServiceNow or having trouble connecting security apps with its infrastructure? For any queries or integration needs related to cybersecurity platforms for your business, please feel free to reach out to us at connect@metronlabs.com.









