The Silent Saboteur: Tackle Schema Misalignment in Cybersecurity Integrations
Learn how to resolve schema misalignment to streamline your cybersecurity platforms.
Vikram

In the high-stakes world of cybersecurity, seamless integration is your organization’s backbone.
Your SIEM system, SOAR platform, EDR solutions, and other critical platforms should all be considered as members of a team. Individually, they’re powerful and talented, but to have a holistic defense, they must speak the same language, share intelligence flawlessly, and act as a unified force.
However, lurking under the surface of even the most sophisticated tech stacks is a quiet disruptor that prevents this desired unity: Schema Misalignment.
It’s the digital equivalent of a poorly choreographed orchestra, where every musician, though brilliant in their own right, is out of sync and off key.
So let’s pull back the curtain on schema misalignment and learn what it truly is, why it is important from an integration standpoint, and how Metron can help your organization with it.
What is Schema Misalignment?
Schema Misalignment, at its core, describes technical discrepancies in how systems structure, label, or format data. Think of it as a structural mismatch that happens when two or more tools, like your SIEM, SOAR, or EDR, misinterpret shared data because their underlying data rules or formats clash.
There are various ways in which such misalignments can manifest themselves. Let’s check out a few of them:
- Different Naming Conventions where your SIEM could flag a suspicious login as “username: jade”, but your SOAR misses it because your playbooks are designed to trigger alerts for “user_id”.
- Varying Data Types where one system logs timestamps as human-readable strings (“2023-10-05T14:30:00Z”), another requires raw Unix epochs (1696523400).
- Structural Differences is yet another one. Imagine that your cloud service nests IP addresses under layers like metadata.geo.location, while your threat intel tool expects a flat source_ip field. They simply won’t see eye to eye.
- Missing or extra fields mean your firewall could export granular geolocation data, but the log aggregator retains only IP_address. This loss of context forces your team to operate in the blind, meaning they can’t quickly validate if an IP belongs to a trusted VPN or a high-risk region.
The list goes on.
Schema misalignment directly impacts operational efficiency and burdens competent teams by having them fix structural gaps - which, truth be told, are tasks that these tools should ideally automate. And so, schema misalignment consequences are major, especially when we think of it from an integration standpoint.
Why is Schema Misalignment Critical in Integrations?
In cybersecurity, accurate and consistent data is non-negotiable. In integrations, where tools must share and act on data in real time, this flaw often becomes catastrophic. We all know, seamless interoperability hinges on aligned schemas and without it, tools continue to operate in silos and stay ignorant to critical context.
Here are a few more critical issues that can take place due to schema misalignment:
- Inaccurate Analysis: When event data isn’t mapped correctly, systems tend to misinterpret the meaning of alerts. Mismatched field names or values distort severity levels, causing critical threats to be misclassified as benign and vice versa. This is especially dangerous for teams relying on AI-driven threat hunting, where inconsistent labels tend to cripple machine learning models.
- Failed Automation: We all know that automation depends on predictable data formats. If integrated tools use conflicting schemas, playbooks and scripts fail to parse required fields or contextual triggers. Hence, analysts are required to intervene in systems that are designed to be hands-off.
- Data Loss or Corruption: This could be a costly one for you, as schema mismatches can force data truncation or transformation during transfers. Vital fields could be dropped, which could result in incomplete or misleading datasets that undermine threat-hunting and reporting accuracy.
How Schema Misalignment Impacts SIEM, SOAR, and EDR
Your SIEM, SOAR, and EDR tools are designed to operate as a seamless security triad, each component amplifying the others’ strengths. But when schema misalignment creeps in, it turns your defense stack into a band of disconnected signals.
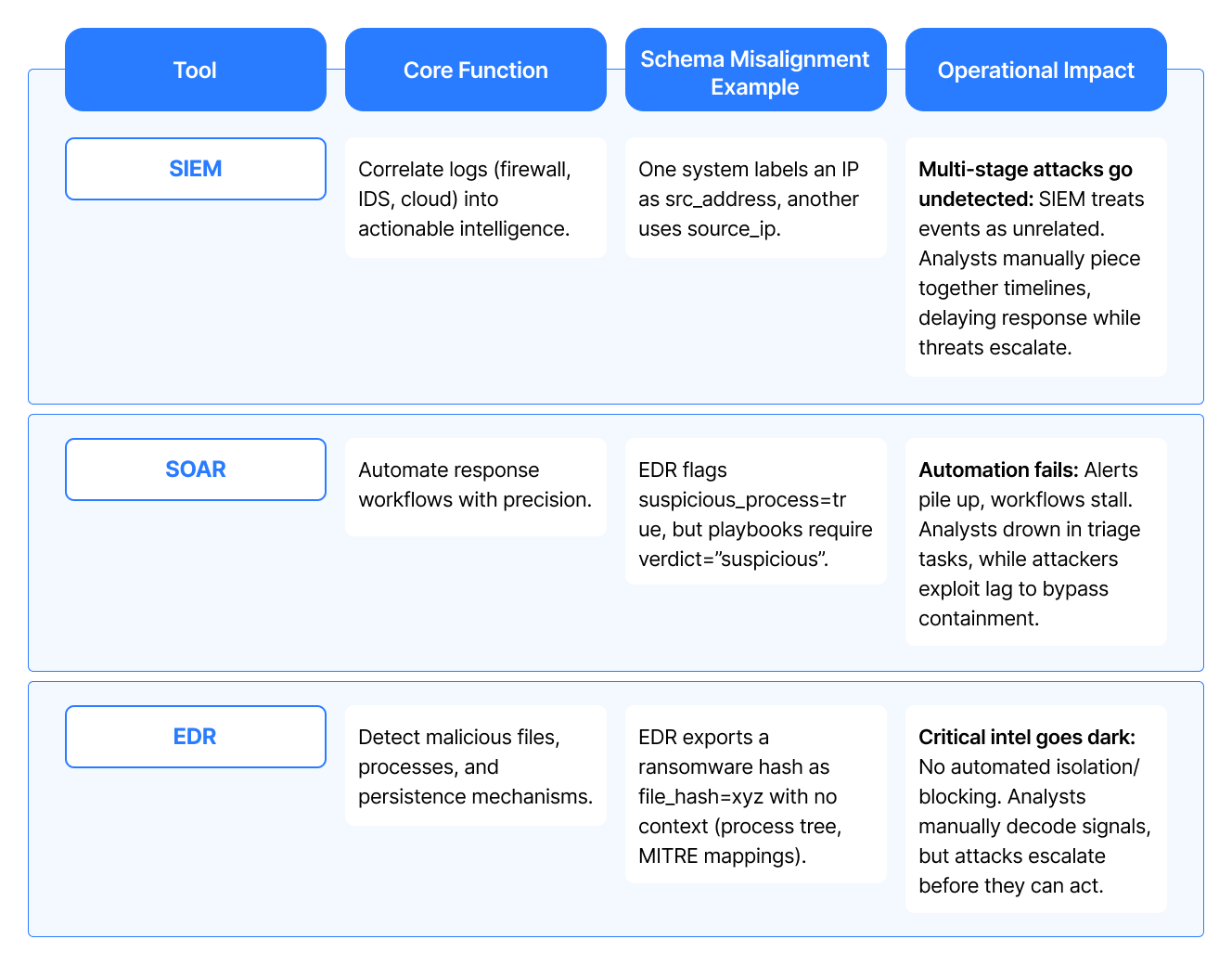
But here’s the good news: aligning your tools doesn’t require a ground-up rebuild. The fix can be much simpler.
How Metron Solves Schema Misalignment
When your SIEM, SOAR, and EDR tools can’t agree on data structure, your team has to jump in to decode alerts instead of acting on them. This automation misfire creates critical gaps, allowing threats to slip through.
Metron directly addresses this challenge, not by replacing your tools, but by enabling them to work seamlessly together. Here’s how:
Decoding the Data Chaos
Every tool has its dialect, and we get that! We audit and document schemas, such as field names, data types, formats, and nested structures, to create a unified blueprint. It’s the foundation that makes your tools understand each other.
Mapping the Data
Once we know how each tool thinks, we build seamless connections between them. This involves field renaming, standardizing data, formatting, enriching, and filtering. Consider a firewall log: it isn’t just an IP address; it’s a potential attacker’s point of origin. Metron ensures that such nuance isn’t lost, using techniques refined through tackling various data annotation challenges.
Transforming Data for Action
Raw mappings aren’t enough. Metron reshapes data to fit each tool’s purpose.
For example, unpacking EDR alerts into SIEM-friendly fields, turning suspicious_process: true into automated investigations. This precision ensures tools get what they need – nothing more, nothing less.
Enforcing Standards
Metron utilizes common standards like OCSF, Google UDM, or Splunk CIM to future-proof your stack. When you onboard a new tool (yes, even that AI-powered one), we make sure it fits in seamlessly without the need for any custom scripts or sleepless nights.
Real-World Testing
We don’t assume it works without rigorously testing it and finding it out for ourselves. Metron stress-tests integrations by:
- Flooding systems with simulated ransomware alerts.
- Validating that every critical field survives transformation.
- Auditing logs to ensure zero data loss or corruption.
Only when alerts trigger flawlessly and timelines stay coherent do we consider it completed.
Conclusion
Schema Alignment isn’t just about fixing data, it’s about fixing outcomes. But it doesn’t have to be this way. With Metron, you can transform your set of fragmented tools into a unified security ecosystem. By bridging data silos, enforcing standards, and automating context-rich transformations, Metron ensures your SIEM, SOAR, EDR, and other tools don’t just share data—they act on it cohesively.
Ready to stop fighting your stack and start fighting threats? Let’s align your tools, not just your data. Drop us a mail at connect@metronlabs.com, and let’s turn schema chaos into your advantage.
Your tools should work for you, not against you. Our team can help make that happen.









