Troubleshooting Microsoft Sentinel Data Ingestion Issues: A Deep Dive
We outline some of the common data ingestion issues with Microsoft Sentinel (and how to troubleshoot them).
Anmol Jain

Introduction to Microsoft Sentinel
Microsoft Sentinel is a cloud-native security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution offered by Microsoft. It provides a comprehensive platform for detecting, investigating, and responding to security threats.
Five Key Features of Microsoft Sentinel
- Data ingestion: Collects data from various sources, including on-premises and cloud-based systems.
- Threat detection: Utilizes advanced analytics and machine learning to detect suspicious activities and potential threats.
- Investigation: Provides tools for in-depth investigation of security incidents, including hunting queries and interactive dashboards.
- Response: Enables automated and orchestrated response actions to mitigate threats and contain incidents.
- Threat intelligence: Leverages Microsoft's threat intelligence to stay informed about emerging threats and best practices.
By leveraging Microsoft Sentinel, organizations can improve their security posture, reduce the time to detect and respond to threats, and gain valuable insights into their security landscape. However, like most applications integrated into complex systems, the increasing complexity of our frameworks opens the door to possible issues and errors that would need to be addressed should they arise.
In the post below, we outline some of the common data ingestion issues your team might encounter when running this app.
Understanding the Problem
When encountering data ingestion challenges in Microsoft Sentinel, it's crucial to identify the root cause accurately and take the appropriate troubleshooting steps.
Common Issues and Solutions
- Logs Not Being Received
- Check Function App Logs:
- Navigate: Access the Microsoft Sentinel portal > Resource Groups > Select the resource group housing the Data Connector > Sort resources by 'Type' > Locate the Function App that you are having issues with.
- Inspect Function: Click on the Function App > 'Functions' > 'ConnectorAzureFunction' > 'Monitor' to view invocation traces.
- Analyze Logs: Examine invocation traces for specific error messages. Common issues include:
- Authentication errors: Verify that the Function App has the correct credentials to access the data source.
- Authorization errors: Ensure that the Function App has sufficient permissions to read and ingest data.
- Network connectivity issues: Check if there are any network-related problems preventing data transfer.
- Data source limitations: Verify that the data source is functioning correctly and not experiencing any issues.
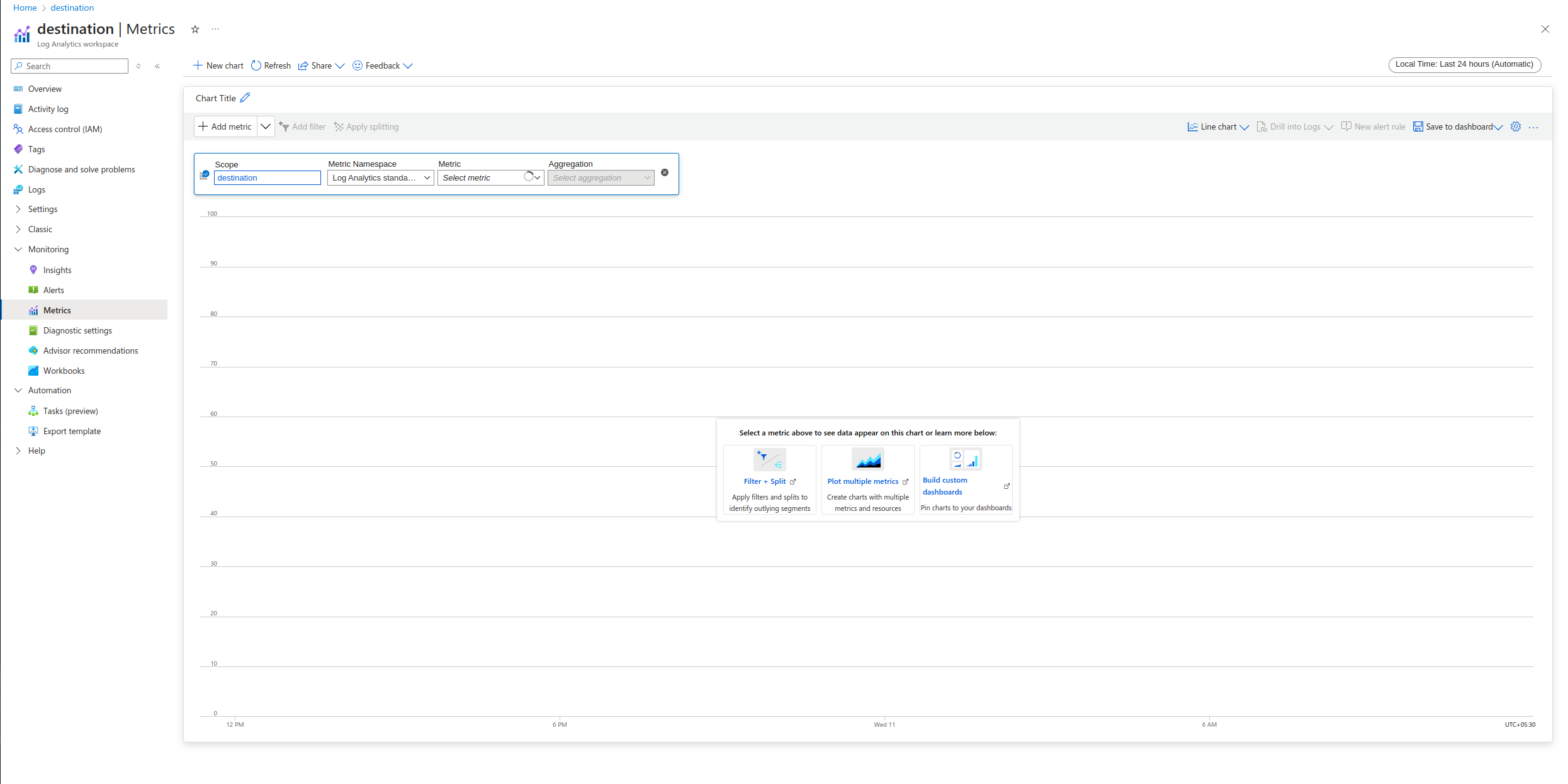
To get an overview and monitor your integration performance, navigate to the Log Analytics workspace associated with your Azure Sentinel environment and access the Insights or Metrics dashboards inside the Monitor section.
- Insights: Provides a comprehensive overview of your data ingestion and processing activities, including data volume, anomalies, and performance metrics.
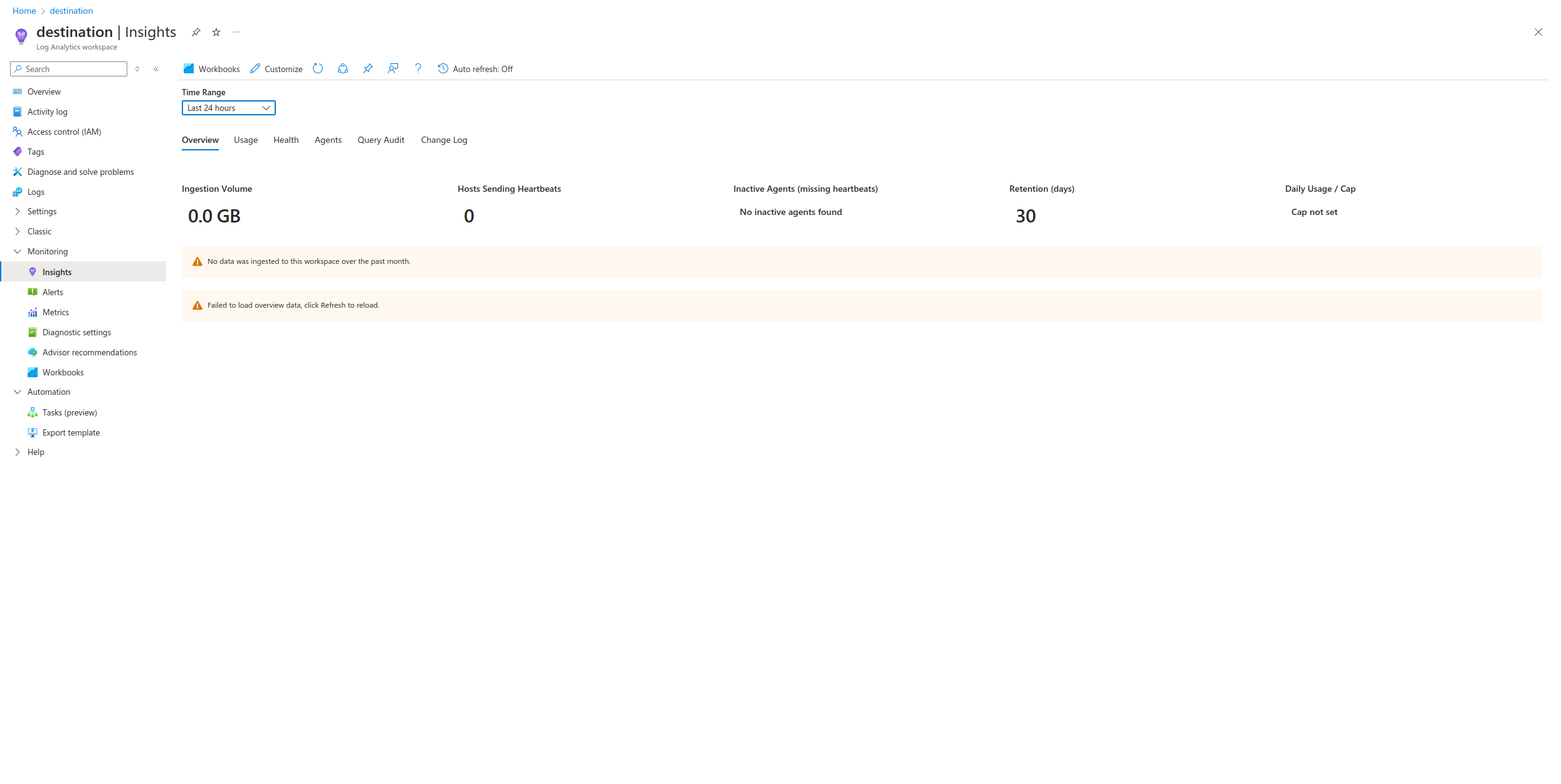
- Metrics: Offers granular metrics for specific aspects of your integration, such as ingestion rates, query execution times, and alert generation.
- Restart Function Apps:
- If you encounter errors, restart both Function Apps. This can often resolve temporary issues or clear cached errors
- Check Function App Logs:
- Incidents Not Being Generated
- Verify Analytics Rule Status:
- Ensure that Analytics Rules are enabled and configured correctly. Check the rule logic and conditions to ensure they match the ingested data.
- Review the rule's severity and threshold settings to verify that incidents are being triggered as expected.
- Inspect Analytics Rule Logs:
- Use the Analytics Rule's logs to identify any errors or warnings that might be preventing incident generation.
- Look for issues related to data ingestion, query execution, or incident creation.
- Verify Analytics Rule Status:
- Sentinel Incident Status Not Updating
- Check Automation Run History:
- Navigate to Microsoft Sentinel portal > 'Automation' > ‘Automation Rules’ or 'Active Playbooks' > Open your relevant playbook or automation.
- Inspect failed playbooks or automation runs for detailed error messages.
- Common issues include:
- Authentication errors: Verify that the playbook has the correct credentials to update the incident status.
- Authorization errors: Ensure that the playbook has sufficient permissions to modify incidents.
- Logic errors: Check the playbook's logic to ensure it is correctly updating the incident status based on the specified criteria.
-
Review Incident Status Update Logic:
- Examine the playbook's/automation’s logic to ensure it is correctly updating the incident status based on the specified criteria.
- Verify that the playbook or the automation is triggered at the appropriate time and with the correct parameters.
- Check Automation Run History:
Additional Considerations
- Review Data Connector Configuration: Ensure the Data Connector is configured correctly and has the necessary permissions.
- Check Network Connectivity: Verify network connectivity between your data source and Microsoft Sentinel, as well as any intermediate firewalls or proxies.
- Monitor Log Analytics Workspace: If using Log Analytics Workspace, monitor its health and storage capacity.
- Consult Microsoft Sentinel Documentation: Refer to the official Microsoft Sentinel documentation for in-depth troubleshooting guides and best practices.
- Utilize Microsoft Sentinel Community: Engage with the Microsoft Sentinel community for support, troubleshooting tips, and shared experiences.
By following these detailed steps and carefully analyzing the logs and configuration, you should be able to effectively troubleshoot data ingestion issues in Microsoft Sentinel and ensure the smooth operation of your security analytics platform.
Considering building an integration with Microsoft Sentinel or any other platform? Metron has experience building scalable integration with Microsoft’s products.
If you are considering any custom cybersecurity solution that focuses on the resources and needs of your organization, please send a note to connect@metronlabs.com.









