Useful Integrations Add-Ons for XSOAR : Fetching Credentials
Fetching credentials is crucial aspect of the management and sharing of credentials, which are used to authenticate and authorize access to resources.
Kshitij Kunte

In today's digital world, security threats are evolving rapidly, and organizations must be able to respond quickly and effectively to protect their assets.
Security orchestration, automation, and response (SOAR) platforms such as XSOAR (formerly known as Demisto) enable organizations to automate and streamline their security operations, making it easier for security teams to detect, investigate, and remediate security incidents.
As businesses continue to rely on technology for critical operations, the need for secure and efficient integration between different systems becomes increasingly important. A crucial aspect of this is the management and sharing of credentials, which are used to authenticate and authorize access to resources.
What is "Fetching Credentials?"
Fetching Credentials is a feature of XSOAR that enables the secure retrieval and sharing of credentials between different systems. With Fetching Credentials, users can configure integration scripts to automatically retrieve credentials from designated sources, such as password vaults or other secure storage locations.
This tool streamlines the integration development process by eliminating the need for manual credential management and reducing the risk of human error. By automating the retrieval of credentials, Fetching Credentials also enhances security by minimizing the exposure of sensitive information.
How Does Fetching Credentials Work?
The Fetching Credentials feature in XSOAR works by leveraging a set of preconfigured scripts that are tailored to work with specific credential sources. These scripts use APIs to retrieve the credentials from the designated sources and provide them to the integration in a secure and controlled manner.
To use Fetching Credentials, users must first configure the integration to use the appropriate script and then specify the credentials that need to be retrieved. Once configured, the integration can securely access the credentials without the need for manual intervention.
Advantages of Using Fetching Credentials
Using Fetching Credentials in integration development provides several advantages, including:
- Enhanced security: By automating the retrieval of credentials, Fetching Credentials reduces the risk of human error and minimizes the exposure of sensitive information.
- Streamlined development: With Fetching Credentials, developers can eliminate the need for manual credential management, saving time and reducing the risk of errors.
- Flexible integration: Fetching Credentials can be used with a variety of credential sources, making it a versatile tool for integrating different systems.
- Better compliance: By automating the retrieval of credentials, Fetching Credentials can help organizations meet compliance requirements by ensuring the secure handling of sensitive information.
Use Case:
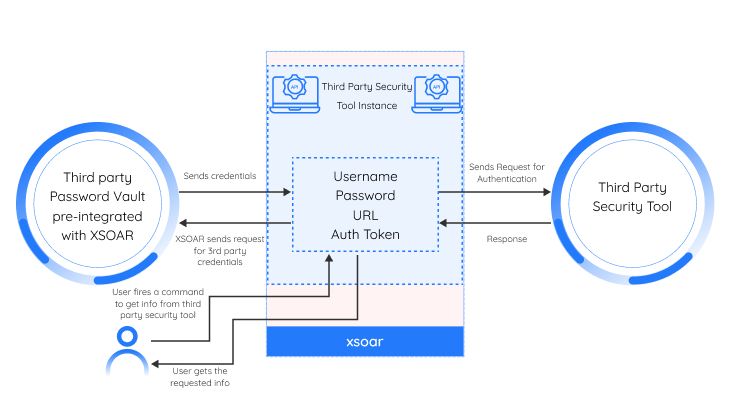
The flow diagram shows the process of integrating a third-party security tool with XSOAR using CyberArk to manage the credentials. This integration enables XSOAR to use the credentials stored in CyberArk to access a third party API and perform actions such as retrieving alerts and incidents, etc.
The flow starts with the CyberArk administrator creating and configuring the Safe, Folder, and Object in CyberArk to store the third party API credentials securely. The XSOAR administrator then sets up the third party integration in XSOAR and maps the required third party API actions to XSOAR commands.
When a user initiates an action that requires access to third party’s, XSOAR first sends a request to CyberArk to retrieve the third party API credentials from the Safe. CyberArk, then, validates the user's identity and retrieves the credentials from the Safe. The credentials are then passed back to XSOAR, which uses them to authenticate and access SentinelOne's API.
After completing the action, XSOAR discards the credentials to ensure they are not stored in memory, and the CyberArk session is closed. This ensures that the third party API credentials are never exposed to XSOAR or the user, providing an added layer of security.
The use of CyberArk to manage credentials in this integration ensures that the credentials are stored securely and are only accessible to authorized users. This reduces the risk of unauthorized access to sensitive data and improves the overall security of the integration.
Overall, this integration provides a seamless and secure way for XSOAR users to access third party API and perform actions without the need to manage and store the credentials themselves.
Conclusion
By automating the retrieval of credentials, Fetching Credentials reduces the risk of human error and minimizes the exposure of sensitive information. This tool also saves time and simplifies the integration development process, making it a valuable asset for businesses looking to improve their operations.
With Fetching Credentials, businesses can ensure the secure handling of credentials and facilitate the integration of different systems, improving their overall efficiency and effectiveness.
Metron Security builds, manages, and supports integrations and custom solutions for leading XDR platforms. Metron has experience working with over 200 security applications. For more information, please reach out to connect@metronlabs.com or explore www.metronlabs.com









