Deep Dive: Unveiling the Architecture of CrowdStrike Falcon
Take a deep dive into the architecture powering Crowdstrike Falcon and its integration capabilities.
Anmol Jain

Well-managed cybersecurity defenses are inevitably the product of teamwork - and not just between the operators of your SecOps team, but also the apps they have at their disposal. The better the integration, the better the communication and coordination in times of incident response and faster action when moving toward the resolution.
In the following post, we take a deep dive into the architecture powering Crowdstrike Falcon and how its integration capabilities can make it a valuable central resource for your organization’s cybersecurity efforts.
The Foundation: Cloud-Native Design for Scalable Integration
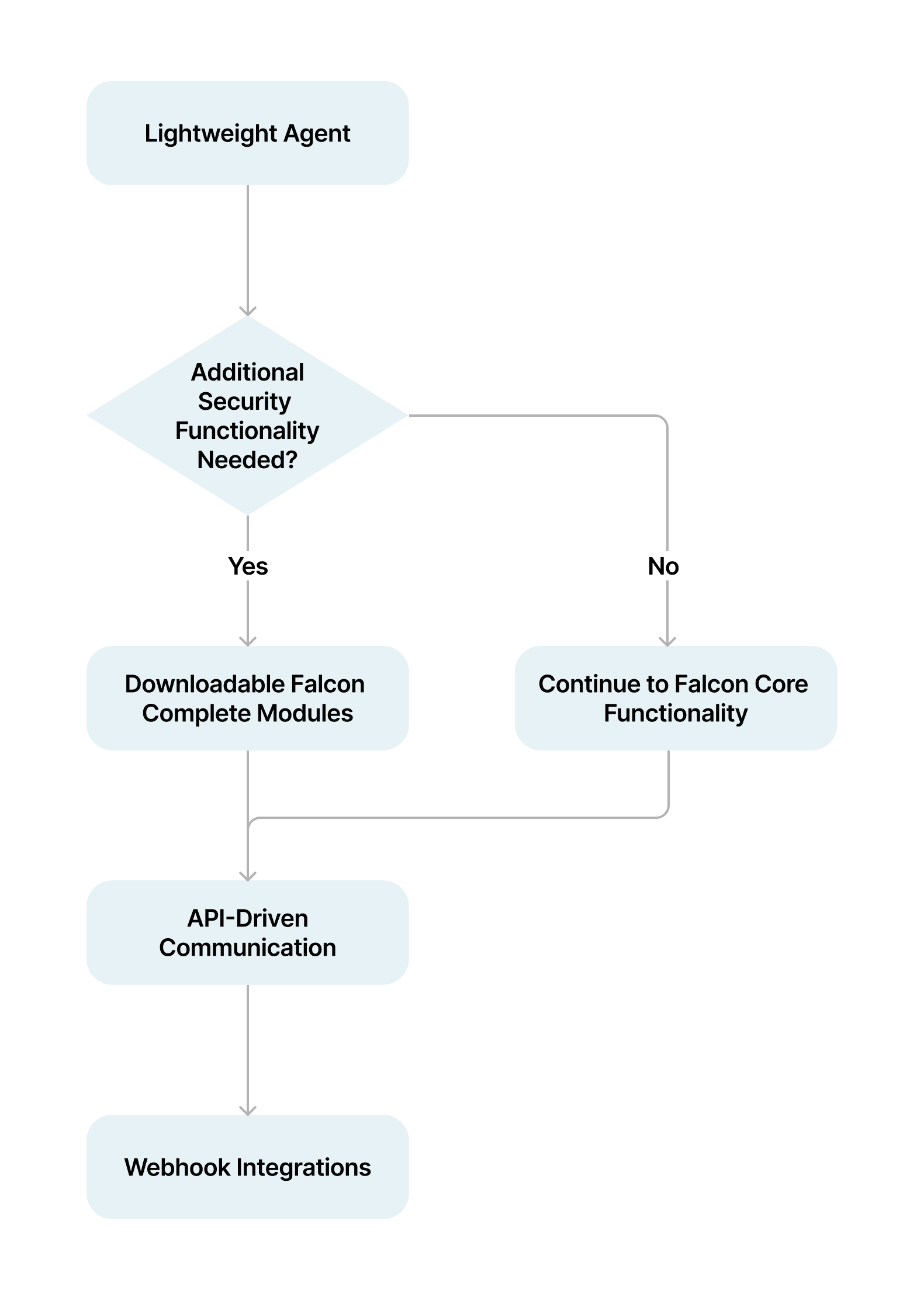
At the heart of Falcon's integration prowess lies its cloud-native architecture. This translates to several key components that empower seamless communication and functionality extension:
- Lightweight Agent: A single, lightweight agent forms the core of Falcon's data collection and enforcement capabilities. This agent can be deployed across all your endpoints without significant resource overhead. Unlike traditional approaches with multiple agents from various vendors, Falcon's agent architecture simplifies deployment and management.
- Falcon Complete Modules: Falcon provides additional security functionalities through downloadable modules within Falcon Complete. These modules leverage the core agent, extending its capabilities without compromising the lightweight design. Integration often happens at the agent level, allowing for granular control over data collection specific to the functionalities enabled by each module.
- API-Driven Communication: Falcon exposes a comprehensive set of well-documented APIs. These APIs act as the communication backbone for external tools and platforms to interact with Falcon's rich data and functionalities. Security teams can leverage these APIs to programmatically access information like threat intelligence, and endpoint status, and even execute security controls on endpoints directly. This allows for deep integration and automation of most security workflows.
- Webhook Integrations: For scenarios requiring immediate action, Falcon offers webhooks. These webhooks act as real-time notification channels. You can configure automated responses triggered by specific security events detected by Falcon. Imagine a critical ransomware attack being detected – a webhook can instantly send a notification to your SIEM system, triggering a pre-defined isolation and remediation workflow.
Openness by Design: Expanding Your Security Landscape
Falcon thrives on an open ecosystem, fostering seamless integration with a vast array of third-party security solutions. This openness complements the cloud-native architecture and is achieved through two primary methods:
- CrowdStrike Store: This online marketplace serves as a one-stop shop for pre-built connectors and applications specifically designed to integrate with Falcon. These pre-built connectors often leverage Falcon's APIs for efficient data exchange and functionality access. They simplify the integration process for security teams, eliminating the need for custom development in many cases.
- Falcon Open XDR: Taking the openness a step further, Falcon Open XDR empowers developers to build custom integrations. It provides Software Development Kits (SDKs) and access to Falcon's core functionalities through well-documented APIs. This allows security professionals to tailor Falcon to their specific needs and seamlessly integrate it with their existing security infrastructure, even if a pre-built connector doesn't exist.
Security Benefits of a Well-Architected Falcon
By leveraging the strengths of its cloud-native architecture and open ecosystem, a well-integrated Falcon can significantly enhance your organization's security posture.
Let’s take a closer look at the benefits:
- Enhanced Threat Detection: Integrate threat intelligence feeds (CTI) to enrich Falcon's native threat detection capabilities. CTI feeds can be incorporated through Falcon Open XDR or pre-built connectors within the CrowdStrike Store. This enables Falcon to identify even the most sophisticated threats by incorporating the latest knowledge.
- Unified Security Operations: Integrate Falcon with your SIEM or SOAR platform. This allows security analysts to view real-time data from Falcon alongside events from other security tools within a single dashboard. This centralized view, facilitated by the underlying architecture, allows for faster and more efficient threat investigation and response.
- Automated Workflows for Faster Response: Utilize Falcon's webhooks and API capabilities to trigger automated workflows within your existing security stack. This can automate crucial actions like isolating compromised endpoints, quarantining threats, or initiating remediation procedures. This minimizes human intervention and ensures a swift response to security incidents, all thanks to the real-time communication channels enabled by the architecture.
Conclusion
Ultimately, by understanding Falcon's architecture and leveraging its openness, you can build a powerful, coordinated security system. Well-built and thought-out integrations can help keep your organization safe from cyberattacks, and empower your teams to respond faster when incidents do occur.
Considering venturing into security automation and integration using Crowdstrike Falcon? Metron has experience integrating multiple security tools with primary systems, along with setting up automation components, including SIEM, SOAR, and XDR solutions.
If you are in need of any custom cybersecurity solution that focuses on the resources and goals of your organization, please send a note to connect@metronlabs.com.









