How Prisma Cloud Strengthens IoT Security
How to use Prisma Cloud to secure IoT deployments.
Shrishthi Dixit

IoT rarely lives in one place.
Devices typically talk to gateways, which run containers/VMs, and land data in cloud-native backends. That sprawl, of course, creates three persistent problems: visibility gaps, config/identity drift, and runtime blind spots.
However, treating IoT-driven workloads as cloud-native security with device/edge context lets you set guardrails before code ships, protect workloads at runtime, and it also makes identities(human and machine) a first-class control surface.
In this post, we talk about securing the cloud-native applications and services (via Prisma Cloud) that ingest and act on IoT data, rather than running security agents on the IoT endpoints themselves.
We’ll take a closer look at how Prisma SASE and Prisma SD-WAN fit into this lifecycle, the recent enhancements that simplify device and branch rollouts and speed up investigations, and how Prisma Cloud secures the cloud-native services powering your IoT data.
Let’s begin!
Note: If you’re new to the platform itself, you may also want to see our guide on Prisma Cloud Security Platform for foundational setup steps.
Prisma Cloud: The Core Building Blocks
- Cloud Security Posture Management (posture & drift): Establish guardrails for encryption, network exposure, storage, IAM least‑privilege, and data protection across accounts/regions. You can also detect drift and route high‑signal findings to owners.
- Cloud Workload Protection (image to runtime): Scan images used on edge gateways and in cloud clusters, block risky images in CI, and enforce runtime policies (process/file/network) with anomaly detection to cut dwell time at the edge and in the cloud.
You can forward Prisma Cloud runtime alerts into Cortex, which uses behavioral analytics across network, endpoint, and cloud data to correlate and investigate those signals more deeply.
- Cloud Infrastructure Entitlement Management (identity right‑sizing): Inventory human and service identities together, detect excessive permissions, and shrink blast radius, especially for machine identities used by device services/gateways.
- Cloud Code Security (shift‑left): Scan Terraform/Kubernetes/serverless manifests and app code for misconfigs, secrets, and vulnerable deps, and enforce policy‑as‑code so non‑compliant changes never ship.
- Application Programming Interface protections: Protect the APIs where device data enters your platform, reducing exposure to weak authentication and authorization, as well as common app/API attacks.
Impact: Unifying Prisma Access, Prisma SD-WAN, Device Security, and Prisma Cloud gives you a consistent policy path from IoT device to cloud workload. In practice, that translates to fewer misconfigurations, cleaner reviews, smoother device/branch rollouts, and fewer runtime surprises because risky changes never ship.
Quick Prerequisites & Notes (High-Level)
Think of this as the pre-flight checklist for your IoT rollout. These quick prerequisites make sure Prisma Access, Device Security, and your SD-WAN fabric are wired up correctly before you start testing policies and visibility.
- Unified management: Use Strata Cloud Manager to onboard SD‑WAN sites directly into Prisma Access natively and manage all your SASE services from a single place centrally.
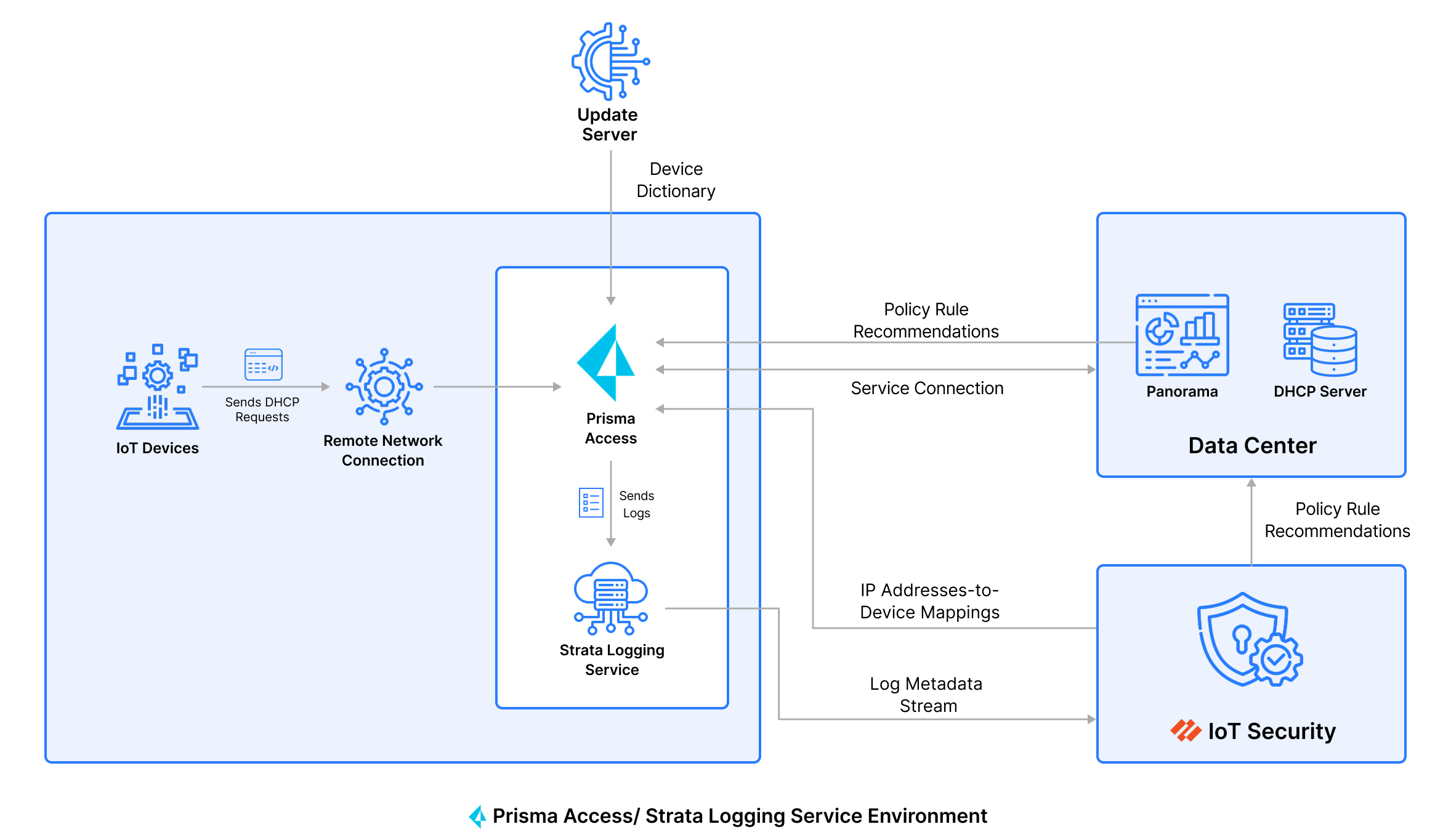
- Device Security and ↔ Prisma Access: Make sure you have the Device Security add-on and that logs are being forwarded correctly. It’s worth reviewing the latest integration checklist in TechDocs to avoid setup gaps. Requires the Device Security add‑on and proper log forwarding; review the latest integration checklist in TechDocs.
- IoT discovery: Set up yourCreate IoT Discovery Profiles, choose whether you want SNMP crawling to be centralized or done per site, and configure the right source interface. decide on centralized vs. per‑site SNMP crawling, and set the source interface.
- VRF segmentation: Define your VRF profiles and any route‑leak rules before attaching your sites. site attachment.
What’s new: SASE and SD-WAN features
These updates are from recent platform enhancements and are especially useful when your IoT devices are located across multiple branches and remote sites.
- Easy onboarding: Prisma SD‑WAN integrated with Prisma Access (native integration): Bulk-onboard SD‑WAN sites into Prisma Access from Strata Cloud Manager. The system automatically selects the nearest Prisma Access location, and you can override this when needed. Remote network objects are built for you, and admins can adjust route advertisements on a per-site basis. This replaces the older CloudBlade-only workflow and makes large-scale rollouts much faster.
- End‑to‑end segmentation with VRF and selective route leaking: If your environment has overlapping IPs (common in M&A) or needs strict per‑tenant or line‑of‑business segmentation, Prisma SD‑WAN VRF lets you define VRF profiles, assign them to sites, bind interfaces/sub‑interfaces, run static or BGP within a VRF, and selectively leak routes between VRFs. This delivers controlled isolation between branches and data centres without needing to redesign branch LANs.
- App SLA Assurance: Move away from device-by-device tweaks and use a policy-based model. Identify applications with App-ID, set latency, jitter, and loss targets, and let the fabric automatically steer flows to paths that meet the required performance. When packet loss is a concern, adaptive FEC can help. The controller also groups many site-level incidents into a single regional event, reducing noise and speeding up root-cause analysis.
- Deeper device discovery using DHCP, ARP, and SNMP crawling: For sites with layered switching or L3 boundaries beyond the SD‑WAN edge, create an IoT Discovery Profile to automate SNMP discovery (version 2 or version 3). You can run discovery centrally using tight SNMP ACLs or distribute the crawl per branch. The discovered devices feed into Device Security, which then works with Prisma Access or NGFWs to enforce allowed behaviours for IoT assets.
How does this improve day‑to‑day operations?
- Faster investigations (lower MTTR): Combining posture, runtime data, identity context, and SASE incidents dramatically shrinks the investigation search space. Many teams also pair Prisma Cloud with a central telemetry platform such as AWS Security Lake for long-term IoT and cloud log retention, which streamlines cross-environment analysis.
- Fewer production errors: IaC and code policies block risky changes before they merge. VRF segmentation helps limit the blast radius when issues do occur.
- Streamlined engineering workflows: Clear policy gates and well‑routed findings reduce “security vs. engineering” loops.
- Better compliance evidence: Continuous posture checks, policy-as-code workflows, and runtime telemetry provide ongoing proof of control rather than one-off audit snapshots.
Field‑tested rollout tips
- Start by establishing posture baselines per account and region. Then add runtime protection and WAAS next–especially where exposure and data sensitivity are highest, such as edge ingress points and APIs.
- Right‑size machine identities early. Mis-scoped service principals are one of the most common sources of accidental over-privilege.
- Block bad IaC before it reaches review. Strong pre-merge checks prevent the painful “rollback and freeze” cycle later.
- Keep your runtime rules easy to understand. Align them with the actual processes, flows, and network paths your services use.
- Integrate with what teams already use: forward Prisma Cloud + SASE/Device Security findings into your existing SIEM/SOAR workflows.
- For deeper cross-stack enrichment (IoT + cloud + network), many teams pair with an XDR platform like SentinelOne Singularity XDR.
- Roll out incrementally: pilot per site/environment; tune, then scale.
These rollout tips are synthesized from Prisma Cloud / Prisma Access best-practice documentation and customer deployments; see linked TechDocs for details.
Bottom line
IoT security is cloud‑native security with device/edge context. Prisma Cloud provides the control plane to prevent risky changes, observe/constrain workloads at runtime, and minimise the blast radius through identity hygiene. Integrating it with Device Security and Prisma Access/SD‑WAN for device discovery and branch enforcement will result in fewer surprises, shorter investigations, and less friction between security and engineering.
We at Metron can help you with just that. Our expertise in building Prisma Cloud integrations with tools like SIEM, SOAR, and more can help bridge your security ecosystem gapsLooking for a custom cybersecurity solution? Please feel free to reach out to us at connect@metronlabs.com, and our team will be happy to assist you.









