SentinelOne Architecture: How Singularity XDR Connects Telemetry, Storyline, and Automated Response
A practitioner’s guide to SentinelOne architecture.
Shrishthi Dixit

These days, security teams rarely struggle with collecting telemetry. After all, endpoints, cloud workloads, identity systems, and third-party tools generate more data than ever. The real challenge is structuring that telemetry into something investigation-ready — and to do so quickly.
SentinelOne’s Singularity platform is built around that principle.
Instead of treating detection, correlation, investigation, and response as separate layers, Singularity integrates them into a unified architecture. Telemetry from endpoints, cloud workloads, identity systems, and third-party sources is ingested, normalized, correlated through Storyline, and operationalized through built-in automation.
This blog explains SentinelOne’s architecture in practical terms, outlining the major building blocks, the location of correlation, the utilization of the data lake, and the role of automation within the response lifecycle.
Let’s take a closer look.
Singularity XDR: The Architecture At a Glance
A simple way to explain SentinelOne’s architecture is as a flow:
- Ingest: Collect native endpoint, cloud, and identity telemetry, and bring in third-party telemetry such as logs, alerts, and security findings (for example, vulnerabilities or misconfigurations).
- Correlate: Connect related events using Storyline.
- Analyze: Hunt and investigate across sources in a unified console.
- Automate: Apply custom detections and response workflows.
- Resolve: Remediate security events, alerts, and findings at machine speed.
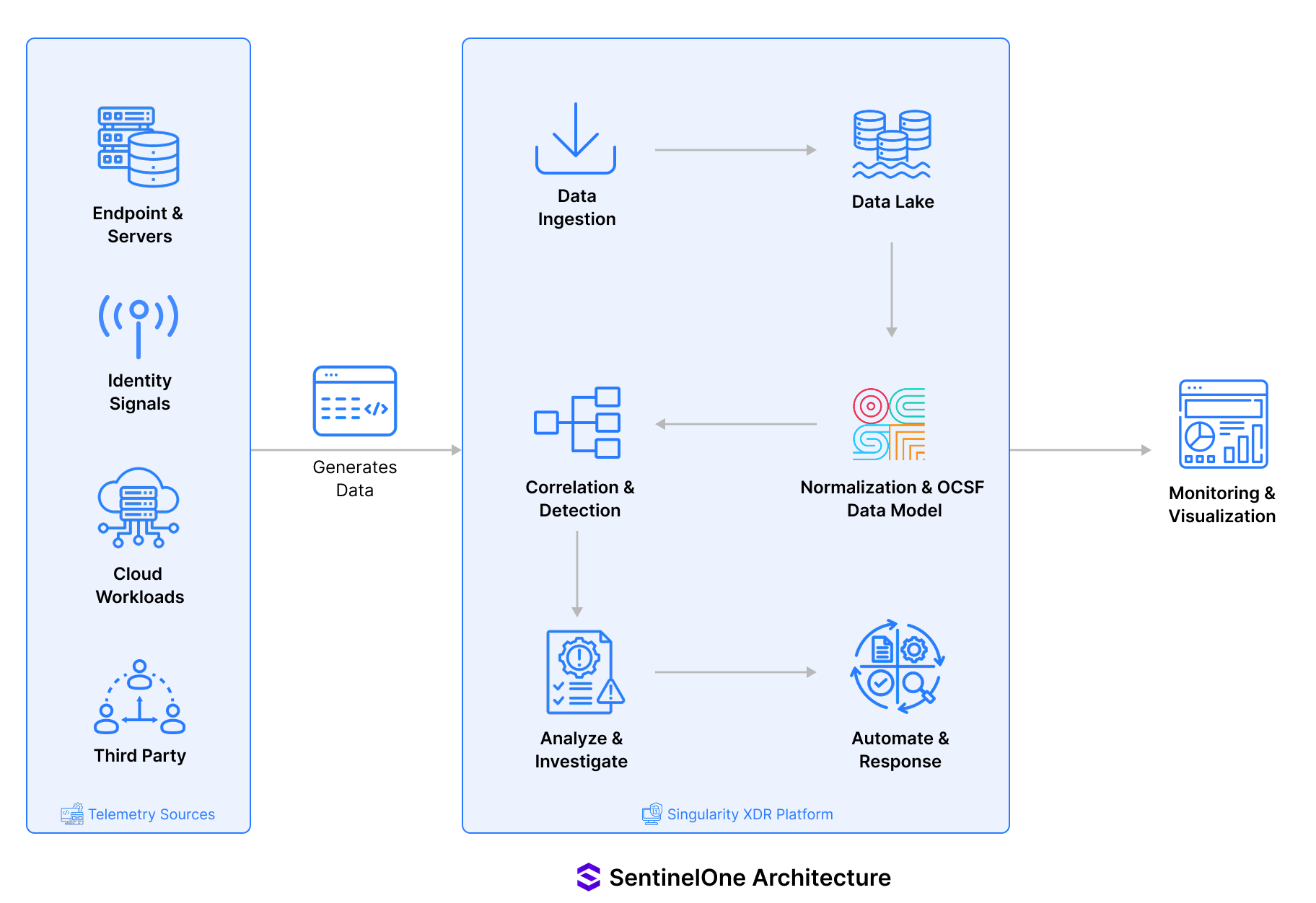
SentinelOne: The Core Building Blocks
1) Telemetry Sources
At the edge of the architecture are the telemetry producers:
- Endpoints and servers
- Cloud workloads
- Identity signals
- Third-party security and IT tools
These sources generate the raw events that later become detections, Storylines, and response actions.
2) Singularity Platform Control Plane (Management + Policy)
Singularity Complete is positioned as a unified platform that provides centralized management and AI-driven prevention, detection, and response. From an architecture standpoint, treat this layer as:
- Central policy and configuration
- Fleet visibility (endpoints/workloads)
- Control surface for detections and response workflows
3) Singularity Data Lake (Storage + Log Analytics)
The data lake is the backbone that makes investigation and detection scalable. SentinelOne frames the data lake as the place where security data can be centralized and used for investigation and analytics. It also highlights normalization using OCSF (Open Cybersecurity Schema Framework) to bring consistency across sources.
In practice, this layer enables:
- Cross-source investigations and hunting
- Longer retention of security data
- Consistent schemas for durable detections and dashboards
4) Correlation and attack reconstruction (Storyline)
Correlation is where architecture turns into operational value. SentinelOne positions Storyline as the mechanism that connects related events into an investigation-ready narrative, reducing the need for manual context-building.
Architecturally, you can think of Storyline as an overlay on top of raw telemetry that produces:
- Linked event sequences
- Causal chains across activities
- Investigation context that drives faster response
5) Detection engineering and automation (response layer)
SentinelOne promotes automation through platform features like Hyperautomation and response capabilities such as kill, quarantine, and rollback (where applicable). It also positions Storyline Active Response (STAR) as an approach to detection logic and response actions.
In architectural terms:
- Detections run against normalized data
- Automated response actions reduce Mean Time to Respond (MTTR)
- Response is policy-driven and repeatable
6) Integrations and ecosystem connectivity (SIEM, ITSM, identity, cloud)
SentinelOne highlights marketplace-style integrations and connectors to pull external raw telemetry (logs, alerts, and findings) into the platform and to connect with other systems (SIEM/SOAR/ITSM, identity providers, cloud services).
A practical way to present this is:
- Inbound integrations: bring logs and signals into Singularity Data Lake
- Outbound integrations: forward alerts/incidents and trigger workflows in external systems
This is also where you decide your operating model:
- XDR-first: Singularity is the primary investigation console
- SIEM-first: Singularity is a major signal provider feeding an existing SIEM/SOAR process
Field-tested rollout tips
- Start with the highest-signal telemetry:Onboard endpoints and identity telemetry first, then add cloud workload signals and the most valuable third-party feeds.
- Pick your schema strategy early:If you want durable detections and consistent dashboards, normalize consistently. Schema-driven approaches age better as you add sources.
- Treat correlation as a primary capability:Build investigations around correlated Storylines rather than raw alerts.
- Add automation with guardrails:Start with low-risk automated actions and approvals, then expand containment as confidence increases.
- Align architecture to your operating model:Decide whether Singularity is your primary hunting console or a strong signal source feeding a SIEM-first workflow.
Bottom line
SentinelOne’s architecture is best understood as a flow: ingest telemetry from endpoint, cloud, and identity sources, normalize it in a scalable data layer, correlate it using Storyline, and drive response through built-in automation and integrations. The operational payoff is less manual context stitching and a faster path from detection to containment.
Considering an XDR-first or SIEM-first design for SentinelOne in your environment? Metron can help map the architecture to your stack, define integration points, and build response playbooks that reduce MTTR and analyst toil. Drop us a note: connect@metronlabs.com









