
Bringing MISP into Google SecOps: A Practical Integration Architecture
Secure your organization by combining MISP and Google SecOps for full identity security.

Secure your organization by combining MISP and Google SecOps for full identity security.

A practical checklist to ensure your Fortinet integrations remain secure and fully optimized after go-live.

A practitioner’s guide to SentinelOne architecture.

A platform-first guide to using the Open Cybersecurity Schema Framework (OCSF).

A practical look at how OT security platforms and Fortinet NGFW combine context and enforcement to improve real-world security operations.

Metron Security announces its participation in the Fortinet Fabric-Ready Technology Alliance, delivering trusted security integrations and automation.

Dive into how FortiSOAR helps your organization to better coordinate its alerts and response.

Explore how Splunk ES can impact your organization's security posture.

How to use Prisma Cloud to secure IoT deployments.

A guide to integrating a CAASM platform with Microsoft Sentinel, ensuring first-class context for detections, hunting, and response.

A detailed guide to build and publish your security app on the CrowdStrike Marketplace using Foundry.

Dive into a practical roadmap for FortiGate, FortiSIEM, and FortiManager integrations.

Get a handle on the process of integrating Fortinet Fortimanager, along with several of its key use cases

How to integrate Google SecOps with third-party platforms like Digital Risk Protection.

Secure your organization by combining Reco AI and CAASM for full identity security.

Discover how integrating XDR with IAM delivers stronger identity security.

Learn how FortiGate web filtering, antivirus, and app control keep your network safe.
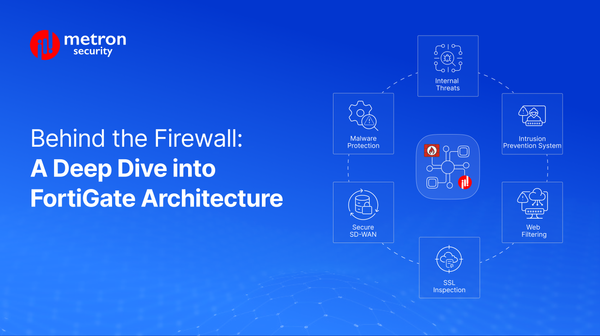
Divine into the FortiGate Architecture from packet flow to real-world use cases

Discover how Breach and Attack Simulation platforms can continuously test your security environment.

A detailed guide to building and publishing your security app on the CrowdStrike Marketplace using Foundry.

Discover why Identity Threat Detection and Response (ITDR) is rapidly gaining traction alongside traditional IAM.

Dive into some of the top use cases that organizations can hope to get out of a next-gen SIEM like Falcon Logscale.

Integrate your security stack with ServiceNow SecOps to streamline detection, automate response, and gain unified visibility across incidents, threats, and IT operations.

Dive into the significance of CCF, its role in cybersecurity, and how you can smoothly implement it for your Service Graph Connectors.

Walk through the architectural design and integration process for connecting BAS platforms with Prisma Cloud CWPP.

OCSF has evolved since initial release. Learn more about its version history.

Integrate Microsoft Sentinel with third-party tools via Azure Function Apps.

Learn how integrating XDR with AWS AppFabric enables unified threat detection, real-time response, and seamless security data flow.

Walk through a step-by-step guide to secure your network with necessary firewall policies using FortiGate.

Discover 5 real-world AWS Security Hub and CSPM integrations.

Discover how Microsoft Sentinel integrations improve unify your security operations at scale.

Rake a closer look at integrating ServiceNow VRM with OT Platforms.