
How to Build and Publish Your App on the CrowdStrike Marketplace
A detailed guide to build and publish your security app on the CrowdStrike Marketplace using Foundry.

A detailed guide to build and publish your security app on the CrowdStrike Marketplace using Foundry.

Dive into a practical roadmap for FortiGate, FortiSIEM, and FortiManager integrations.

How to integrate Google SecOps with third-party platforms like Digital Risk Protection.

Secure your organization by combining Reco AI and CAASM for full identity security.

Discover how integrating XDR with IAM delivers stronger identity security.

Learn how FortiGate web filtering, antivirus, and app control keep your network safe.
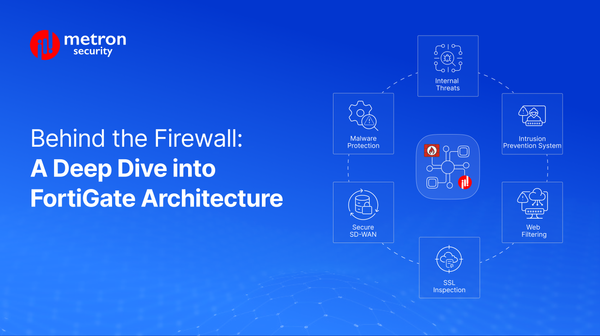
Divine into the FortiGate Architecture from packet flow to real-world use cases

Discover how Breach and Attack Simulation platforms can continuously test your security environment.

A detailed guide to building and publishing your security app on the CrowdStrike Marketplace using Foundry.

Discover why Identity Threat Detection and Response (ITDR) is rapidly gaining traction alongside traditional IAM.

Dive into some of the top use cases that organizations can hope to get out of a next-gen SIEM like Falcon Logscale.

Integrate your security stack with ServiceNow SecOps to streamline detection, automate response, and gain unified visibility across incidents, threats, and IT operations.

Dive into the significance of CCF, its role in cybersecurity, and how you can smoothly implement it for your Service Graph Connectors.

Walk through the architectural design and integration process for connecting BAS platforms with Prisma Cloud CWPP.

OCSF has evolved since initial release. Learn more about its version history.

Integrate Microsoft Sentinel with third-party tools via Azure Function Apps.

Learn how integrating XDR with AWS AppFabric enables unified threat detection, real-time response, and seamless security data flow.

Walk through a step-by-step guide to secure your network with necessary firewall policies using FortiGate.

Discover 5 real-world AWS Security Hub and CSPM integrations.

Discover how Microsoft Sentinel integrations improve unify your security operations at scale.

Rake a closer look at integrating ServiceNow VRM with OT Platforms.

Discover how data normalization with Google SecOps' UDM boosts threat detection.

Learn how to resolve schema misalignment to streamline your cybersecurity platforms.

Discover how CrowdStrike Falcon integration helps stop complex attacks across hybrid and cloud environments.

Learn how to integrate CI alerts into Google SecOps SIEM to boost IoT/OT visibility.

Expert strategies to maintain, test, and future-proof your Splunkbase app.

Discover how data annotators can become a versatile asset across your organization's range of ML applications.
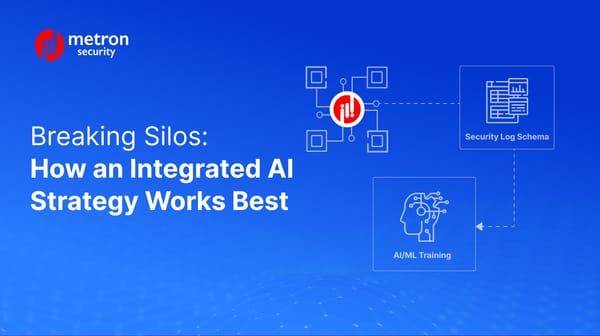
Explore how an integrated approach to AI/ML can transform your security operations.

Discover how log annotation fuels AI accuracy in cybersecurity.

Discover how a CASB integration can protect your next-gen AI Agent tools.

Explore how data annotation hurdles can impact cybersecurity outcomes (and how to overcome them).

Everything you need to know about the latest Splunk critical updates.

Discover Log Forge, a lightweight HTTP REST API server designed to mimic the real API of a specific cybersecurity platform.

Dive into five real-world use cases for integration Google SecOps with EDR.

Discover how Metron's Schema Vault can help ensure accurate data annotation.
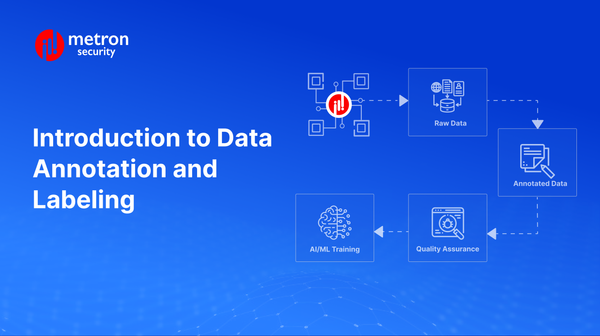
Dive into how data annotation and labeling in cybersecurity fills key industry gaps and benefit AI.

Sentinel can act as your organization's security control tower when paired with a Digital Risk Platform (DRP). Learn how!

A well-integrated and seamless security ecosystem is no longer simply optional.

AWS CloudWatch boosts security when integrated with the right tools. From detecting threats with Sentinel to automating response with XSOAR, see how these integrations enhance cloud protection.

Metron Code Jam February 2025: A thrilling fusion of coding, collaboration, and cybersecurity innovation!

Discover how your team can make the best use of the NVD-CVE Fetcher-APP for Splunk.
Metron Code Jam January 2025: A thrilling fusion of coding, collaboration, and cybersecurity innovation!

We outline some of the common data ingestion issues with Microsoft Sentinel (and how to troubleshoot them).

Discover JupiterOne’s vital features, benefits, and integration capabilities among others.

Troubleshoot common Cybereason EPP-SIEM integration errors.

Aiming to get your app/integration solution published to Splunkbase?

As we come to rely more and more on cloud services, ensuring that your environment is running smoothly can often feel like a juggling act. Fortunately, tools such as AWS Cloudwatch can help streamline this process, by providing an observability solution that enables you to track and respond to performance

Discover how Metron's expertise in BAS integrations can help you achieve a seamless and successful integration with SafeBreach.

Take a closer look at the key components of XDR.

Take a closer look at some of the most common Splunk usages and how to troubleshoot frequently-seen errors that might occur.

Take a closer look at ServiceNow Vulnerability Response and its key use cases.

Get a handle on the process of integrating Fortinet Fortimanager, along with several of its key use cases

Discover how the OSCF framework benefits your data normalization processes.

Dive into the various cybersecurity use cases of Prisma Cloud.

Discover 5 compelling use cases for your XDR integration.

A detailed walkthrough for troubleshooting common issues encountered with AWS Security Lake.

Discover how OCSF helps break down data silos and streamlines inter-application communication.

Take a closer look at the features and availability of the Logpoint SIEM.

Take a deep dive into the architecture powering Crowdstrike Falcon and its integration capabilities.

Learn how to how to fetch logs from Amazon Security Lake.

Explore the ways and benefits of integrating your SIEM platform with Microsoft Defender XDR

Explore how Security Lake and an XDR platform can work together to offer enhanced protection to your organization.

Metron is pleased to announce it is helping to secure enterprise networks with HPE.

We discuss leveraging some of the tools and measures offered by Palo Alto Networks for network security.

We dive into the OCSF framework and its ability to standardize the language of your data.

Dive into the technical considerations for integrating OT platforms with IT systems.

Discover the various Cortex offerings and learn how they can become potential game-changers in your security ecosystem.

Prisma Cloud offers a comprehensive cloud security platform. Find out how to integrate it into your ecosystem!

Discover whether Sumo Logic's SIEM offering could become a valuable tool for your organization.

Discover whether Splunk's SIEM offering is right for your organization.
![FortiGate (NGFWs by Fortinet) Installation Guide [2024]](/content/images/size/w600/2025/11/FortiGate--NGFWs-by-Fortinet--Installation-Guide--2024-.png)
Today, we walk you through an on-prem installation process for setting up the FortiGate NGFW.
![How to Set Up IBM QRadar SIEM on a Standalone VM [2024]](/content/images/size/w600/2025/11/How-to-Set-Up-IBM-QRadar-SIEM-on-a-Standalone-VM--2024-.png)
We walk you through setting up your IBM QRadar SIEM using a standalone virtual machine.

Cyber threats are always evolving. Discover how SentinelOne Singularity XDR can become a key asset in your defenses against cyber threats.
FortiGate is one of the many apps available through the wider Fortinet security suite. In the following post, we’ll walk you through the key elements of this application, its use cases, and what it’s like to configure.

Within Splunk’s architecture, numerous elements can automate and integrate key security functions. Discover how this tool can empower your organization.
![Amazon Security Lake: Integration Architecture Overview [2024]](/content/images/size/w600/2025/11/Amazon-Security-Lake_-Integration-Architecture-Overview--2024-.png)
In the following piece, we provide a high-level overview of the integration architecture for this tool. Read the details here.

To take advantage of the opportunities offered by the many use cases of ServiceNow ITSM, it is important that you are first not only aware of this platform but also how it functions.

OCSF is a framework with a strong potential for unifying cybersecurity systems across platforms. Learn more about its usage here.

IBM QRadar is a Security Information and Event Management (SIEM) solution. Here are some of the top use cases to unlock your security potential.
The ServiceNow Store is the central repository for workflow apps and certified integrations. Learn how to publish your app on this platform.
![Your Guide to Amazon Security Lake and its Use Cases [2024]](/content/images/size/w600/2025/11/Your-Guide-to-Amazon-Security-Lake-and-its-Use-Cases--2024-.png)
In the following post, we examine one of the most prominent data lakes available - Amazon Security Lake.

In the following post we walk you through how to fetch logs in this platform.

Looking for a cloud-native SIEM but unsure where to begin? Become familiar with Exabeam’s Fusion offering here.

ServiceNow ITSM is a cloud-based IT Service Management (ITSM) tool that helps businesses streamline their IT operations. It automates many IT tasks, such as incident resolution and problem management, which frees up IT staff to focus on more strategic initiatives. The platform is based on ITIL (Information Technology Infrastructure Library)

In the following post, we discuss tips and considerations for connecting your SIEM with AWS for efficient cloud security and optimization.

Looking for a SIEM but uncertain where to begin? Become familiar with FortiSIEM and if it's the right choice for your organization.
SOAR platforms can act as the central hub for your security needs. We outline 6 important factors to consider for SOAR adoption as we move into 2024.

Companies are increasingly automating essential security operations center (SOC) tasks. In the following guide, we outline 5 SOAR use cases for your SOC.

In this short post, we dive into five key use cases that highlight the indispensable role a well-integrated SIEM plays in enhancing an organization's threat hunting capabilities.

We discuss some of the benefits of pairing your SIEM with a threat intelligence platform, such as Recorded Future, ThreatConnect, Zerofox, Anomali and many more.

In this guide, we will detail five critical components of XDR integration along with their potential challenges and resolutions.

We're pleased to announce that our API monitoring tool is now available!

In the following article, we will walk you through setting up your copy of IBM resilient as well as ensuring App Host is paired and enabled.
In the following guide, we'll walk you through installing Splunk SOAR using a virtual machine and Linux.

With OCSF, a vendor-agnostic core security schema is now available, enabling a common approach to data sharing among different tools.
![Setting up IBM QRadar SOAR (Formerly Resilient) on a standalone VM [2023]](/content/images/size/w600/2025/11/Setting-up-IBM-QRadar-SOAR--Formerly-Resilient---on-a-standalone-VM.png)
In the following guide, we will walk you through setting up IBM Resilient using a standalone virtual machine.

Are you having issues troubleshooting or setting up your AWS platform? In the following article, we'll walk you through creating an IAM for Splunk-SOAR from an ova file using Amazon Web Services (AWS).
In this case study, we explore how a large manufacturing company addressed the security concerns of their wireless IoT devices through integration.

In this post we discuss how a Splunk Enterprise application that could integrate with OT & IoT Security applications for better security.

This following guide outlines the steps needed to set up QRadar on AWS for development purposes.
Fetching credentials is crucial aspect of the management and sharing of credentials, which are used to authenticate and authorize access to resources.
![How to Setup ArcSight on EC2 [2023 Walkthrough]](/content/images/size/w600/2024/04/How-to-Setup-Up-ArcSight-on-EC2--2023-Walkthrough-.png)
The following article will provide the step-by-step guidelines for setting up Arcsight logger on EC2.

This article focuses on the trends in XSOAR that readers who are familiar with the platform will likely find helpful for the coming year.
![XSOAR Debugging Solutions for Common Problems [Part 1]](/content/images/size/w600/2025/11/XSOAR-Debugging-Solutions--for-Common-Problems---Part-1-.png)
In the post below, we have outlined some of the common issues we’ve come across among our XSOAR users.

Metron Security has announced its successful completion of the Service Organization Control (SOC) 2 Type 1 audit of the suitability of its relevant security controls.
This guide explains how to get started with installing a Splunk SOAR for your security ecosystem.

This article walks through the steps needed to update/deploy your ServiceNow app into a QA Instance. To do so, we will be using the Development instance as the source.

We give ChatGPT a few spins at answering questions about XDR.

The goal of this article is to help users understand how data flows when we configure an integration.

Cortex XSOAR is designed to accommodate integrations whether it be from a custom solution or through the tools available in the app.

IBM Security QRadar Community Edition (CE) is a free and full-featured - albeit lighter -version of QRadar based on version V7.3.3. This edition is also specifically designed for students, app developers, and security professionals in need of a testing environment

In this post we detail a few of the common ways you can troubleshoot issues with your Cortex XSOAR application.

Logs can be retrieved for troubleshooting in IBM QRadar SOAR as needed and outlined in the steps below.

In the post below, we detail two different methods of extracting your log files from the platform.

The Cortex XSOAR Marketplace is the central hub where users can browse, purchase and deploy integrations between the main platform and third-party apps.

Splunk is widely used for its log retrieval and data sharing abilities, and is commonly integrated with a variety of tools such as SaaS cloud software like ServiceNow.

Splunk Enterprise 9.0 has just been rolled out and there are a plethora of new features and updates (both major and minor) to be noted with this release.

In this post, we'll focus on two use cases that can help improve your team's responsive time when reviewing application logs.

Why are security operators turning towards data enrichment and the ways to automate the process more than ever before?

As talented as your security operations team may be, the best way to empower them is through automation.

Data enrichment is the Holy Grail of the security industry. All platforms - and especially the newer platforms to hit the market - are only as meaningful as the data they ingest.

2021 was a record year for cyber threats, with both the number and severity of attacks reaching all time highs.

Security Orchestration, Automation, and Response (SOAR) solutions play a critical role in security automation and an integral part in most major cybersecurity team's workflows.

Incident response and prevention are key concerns of any security team.

There’s no single way to handle it for every situation, but we’ve detailed a few examples of highly scalable approaches to maintaining 3rd party ecosystems below.

Few organisations rely on a single app, software, or workflow to manage their day-to-day operations as well as its long term growth. Your organisation most likely benefits from anywhere from a half-dozen to close to a hundred different apps, depending on your size and industry.

While there are countless use cases, here are three security use cases where SOAR tools can react faster than manual intervention and empower your SOC teams to better manage threats.

Infrastructure companies, which have seen a record rise in ransomware attacks targeting their systems since 2019, have remained the primary targets for the operators behind Ragnar Locker.

Cybersecurity breaches and ransomware attacks in particular are costing organisations a fortune.

In the following blog post, we detail how to configure AttackIQ on a Linux machine as well as set up Agents on Windows.

Cortex XSOAR keeps a detailed list of logs that are automatically generated when activities take place in the environment, such as when issues arise or for verifying system information.

SOAR is an acronym for Security Orchestration, Automation and Response.

This post describes how to set up a test environment over a virtual machine (VM) using the Cybereason console.

You can retrieve your logs as well as your log archives using the app. We’ve detailed the main steps you’ll need below.

Industry insiders and commentators are highlighting 2022 as the year when cybersecurity comes home.

Custom integration apps for QRadar can be submitted to the IBM Security App exchange for greater usage and visibility

This post outlines the software design and architecture necessary for building a custom integration application between QRadar and a generic security sensor.

Splunk is a versatile app that keeps records of most events that take place within your app. Find out how to fetch your Splunk logs here.

Before we can use the Universal REST API DSM and Protocol in QRadar, we have to install the Protocol so that it appears in the list of supported protocols. The installation is usually straightforward, but we have seen some issues with installing the protocol on some machines.

Are you using the latest app version for your integration? How do you find out?

Before you can act on threats, you have bring your security data into your QRadar deployment.

There are several ways to verify the successful operation of a function. You can also use these ways to troubleshoot a problem with your Resilient app.

Facing issues with a QRadar app? Did you know that you can fetch the application logs.

Connectors and parsers built by Metron Labs which includes IBM QRadar, Splunk, Phantom, ServiceNow and IBM Resilient and middleware connector built by Metron for API only access security applications.

Metron’s Integration Exchange Framework is designed to manage and maintain all third party security applications.

This case study outlines how Crowdstrike integrates with IBM QRadar and its use cases.